perlapp exe 分析
通过script定位
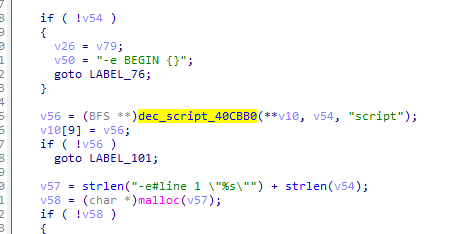
跟进,定位extract
void *__fastcall dec_script_40CBB0(BFS *res_bfs, const char *fname, const char *a3)
{
// [COLLAPSED LOCAL DECLARATIONS. PRESS KEYPAD CTRL-"+" TO EXPAND]
StackCookie = qword_4162E8;
buffer = 0i64;
if ( (unsigned int)getFile_inbfs_406D10(res_bfs, (char *)fname, strlen(fname), &fileinfo) )
{
if ( fileinfo.compressdata_offset20 )
{
if ( fileinfo.res_bfs_0->endian == 0x2000000 )
uncompsize = ((fileinfo.compressdata_offset20->uncompsize & 0xFF00 | (fileinfo.compressdata_offset20->uncompsize << 16)) << 8) | ((HIWORD(fileinfo.compressdata_offset20->uncompsize) | fileinfo.compressdata_offset20->uncompsize & 0xFF0000) >> 8);
else
uncompsize = fileinfo.compressdata_offset20->uncompsize;
}
else
{
uncompsize = 0;
}
v6 = uncompsize + 1;
buffer = malloc(v6);
if ( !buffer )
{
sprintf(Buffer, "Panic: Can't alloc %lu bytes for %s", (unsigned int)v6, a3);
sub_409930(Buffer);
}
if ( !buffer )
return 0i64;
EnterCriticalSection(&CriticalSection);
if ( !extract_4067C0(&fileinfo, buffer) ) // buffer-->得到 perl 脚本内容
{
LeaveCriticalSection(&CriticalSection);
sub_409930("Panic: Can't extract %s", a3);
free(buffer);
return 0i64;
}
LeaveCriticalSection(&CriticalSection);
*((_BYTE *)buffer + uncompsize) = 0;
}
return buffer;
}
todo
解析资源中的BFS可得到所有脚本,有时间跟一下结构
参考链接:
从PDK打包的可执行程序里面解出完整的Perl源码 - 『脱壳破解区』 - 吾爱破解 - LCG - LSG |安卓破解|病毒分析|www.52pojie.cn



 浙公网安备 33010602011771号
浙公网安备 33010602011771号