实验环境
本实验基于CentOS7.3 操作系统,总共5台设备,两台做后端web服务器,两台做lvs和keepalived,一台做客户机,实验以LVS(DR)+Keepalived和LVS(NAT)+Keepalived两种模式来做双机热备份,实验环境拓扑如下图所示:

上图为DR+keepalived模式拓扑,NAT+keepalived模式,在两台lvs调度器上分别新添加了一张网卡,拓扑与上图类似
DR+keepalived模式
1.配置后端web服务器
Web_Server1
基本配置:
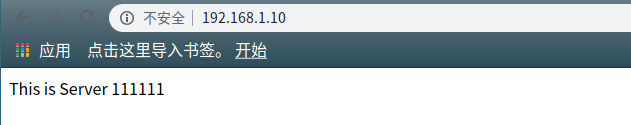
yum -y install epel-release //安装Nginx源 yum -y install nginx //安装Nginx systemctl start nginx //启动Nginx服务 systemctl enable nginx //加入开机自启 mv /usr/share/nginx/html/index.html /usr/share/nginx/html/index.html_bak //备份原有默认页面 vi /usr/share/nginx/html/index.html //测试页面 This is Server 111111 //测试页面内容 为了便于实验验证,关闭防火墙和selinux systemctl stop firewalld setenforce 0
验证:
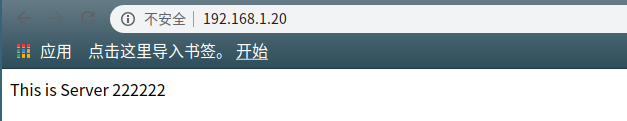
Web_Server2,配置同上,唯一不同的地方就是测试页面的内容,可以设置为“This is Server 222222”便于验证,配置完后的验证结果如下:
2.配置LVS
LVS1
yum -y install keepalived* ipvsadm //安装keepalived和lvs管理工具 modprobe ip_vs //加载内核模块 mv /etc/keepalived/keepalived.conf /etc/keepalived/keepalived.conf_bak //备份配置文件 vi /etc/keepalived/keepalived.conf //配置keepalived和DR global_defs { router_id LVS_TEST #服务器名字 } vrrp_instance VI_1 { state MASTER #配置主备,备用机此配置项为BACKUP interface ens33 #指定接口 virtual_router_id 51 #指定路由ID,主备必须一样 priority 101 #设置优先级,主略高于备份 advert_int 1 #设置检查时间 authentication { auth_type PASS #设置验证加密方式 auth_type 1234 #设置验证密码 } virtual_ipaddress { 192.168.1.100 }
} virtual_server 192.168.1.100 80 { delay_loop 15 #健康检查时间 lb_algo rr #LVS调度算法 lb_kind DR #LVS工作模式 !persistence 60 #是否保持连接,!不保持 protocol TCP #服务采用TCP协议 real_server 192.168.1.10 80 { weight 1 #权重 TCP_CHECK { #TCP检查 connect_port 80 #检查端口80 connect_timeout 3 #超时时间3秒 nb_get_retry 3 #重试次数3次 delay_before_retry 4 #重试间隔4秒 } } real_server 192.168.1.20 80 { weight 1 TCP_CHECK { connect_port 80 connect_timeout 3 nb_get_retry 3 delay_before_retry 4 } } }
为了方便实验验证关闭防火墙和selinux
systemctl stop firewalld
setenforce 0
重启keepalived服务
systemctl restart keepalived
systemctl enable keepalived
通过ip a验证虚拟IP是否生效
[root@lvs1 ~]# ip a 1: lo: <LOOPBACK,UP,LOWER_UP> mtu 65536 qdisc noqueue state UNKNOWN group default qlen 1000 link/loopback 00:00:00:00:00:00 brd 00:00:00:00:00:00 inet 127.0.0.1/8 scope host lo valid_lft forever preferred_lft forever inet6 ::1/128 scope host valid_lft forever preferred_lft forever 2: ens33: <BROADCAST,MULTICAST,UP,LOWER_UP> mtu 1500 qdisc pfifo_fast state UP group default qlen 1000 link/ether 00:0c:29:1c:36:0f brd ff:ff:ff:ff:ff:ff inet 192.168.1.30/24 brd 192.168.1.255 scope global noprefixroute ens33 valid_lft forever preferred_lft forever inet 192.168.1.100/32 scope global ens33 #虚拟IP valid_lft forever preferred_lft forever inet6 fe80::e407:238a:8fd0:2ee8/64 scope link noprefixroute valid_lft forever preferred_lft forever
LVS2的配置同LVS1,只需将配置文件中下面两处修改即可
global_defs { router_id LVS_TEST } vrrp_instance VI_1 { state BACKUP #类型为备份 interface ens33 virtual_router_id 51 priority 99 #优先级 advert_int 1 authentication { auth_type PASS auth_type 1234 } virtual_ipaddress { 192.168.1.100 } } virtual_server 192.168.1.100 80 { delay_loop 15 lb_algo rr lb_kind DR !persistence 60 protocol TCP real_server 192.168.1.10 80 { weight 1 TCP_CHECK { connect_port 80 connect_timeout 3 nb_get_retry 3 delay_before_retry 4 } } real_server 192.168.1.20 80 { weight 1 TCP_CHECK { connect_port 80 connect_timeout 3 nb_get_retry 3 delay_before_retry 4 } } }
关掉主服务器的keepalived服务,验证备份的keepalived是否生效
[root@lvs2 ~]# ip a 1: lo: <LOOPBACK,UP,LOWER_UP> mtu 65536 qdisc noqueue state UNKNOWN group default qlen 1000 link/loopback 00:00:00:00:00:00 brd 00:00:00:00:00:00 inet 127.0.0.1/8 scope host lo valid_lft forever preferred_lft forever inet6 ::1/128 scope host valid_lft forever preferred_lft forever 2: ens33: <BROADCAST,MULTICAST,UP,LOWER_UP> mtu 1500 qdisc pfifo_fast state UP group default qlen 1000 link/ether 00:0c:29:97:50:6a brd ff:ff:ff:ff:ff:ff inet 192.168.1.40/24 brd 192.168.1.255 scope global noprefixroute ens33 valid_lft forever preferred_lft forever inet 192.168.1.100/32 scope global ens33 #虚拟IP漂到备份服务器上了 valid_lft forever preferred_lft forever inet6 fe80::422b:2205:9d05:215d/64 scope link noprefixroute valid_lft forever preferred_lft forever
验证DR是否生效
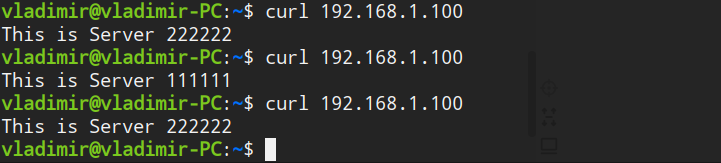
NAT+keepalived模式
说明:NAT模式的话,两个lvs调度器分别需要两张网卡,一张用来连接内部web服务器,一张模拟外网,其他配置跟DR+keepalived模式一样,只需给两台lvs调度服务器分别添加一张网卡,在keepalived配置文件中再添加一个虚拟IP,将lvs模式从DR修改成NAT即可,具体操作步骤如下:
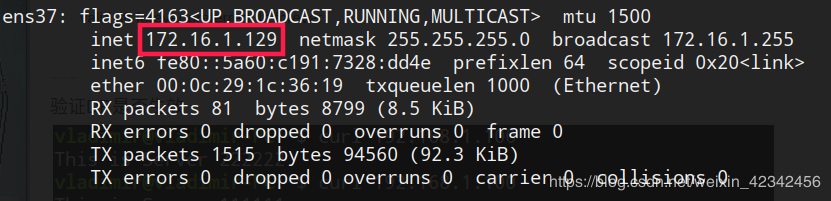
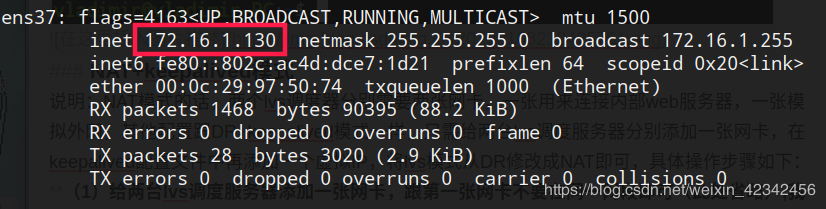
1.给两台lvs调度服务器添加一张网卡,跟第一张网卡不要在同一网段即可(此处省略),我添加网卡的网段如下:
LVS1
LVS2
2.其他要安装的包和需要关闭的东西和前面DR+keepalived模式一样(此处省略),唯一不同的是需要在两台LVS调度器上启用路由转发功能,具体操作如下:
echo "1" > /proc/sys/net/ipv4/ip_forward
3.修改keepalived配置文件,大致内容与DR+keepalived模式一样,具体要修改的地方如下:
LVS1
vi /etc/keepalived/keepalived.conf ...... vrrp_instance VI_1 { state MASTER interface ens33 virtual_router_id 51 priority 101 advert_int 1 authentication { auth_type PASS auth_type 1234 } virtual_ipaddress { 192.168.1.100 } } # 再原来DR+keepalived模式的基础上添加一个虚拟IP vrrp_instance VI_2 { state MASTER interface ens37 #指定接口为新添加的网卡 virtual_router_id 51 priority 101 advert_int 1 authentication { auth_type PASS auth_type 1234 } virtual_ipaddress { 172.16.1.100 } } # 这一块将原来的192.168.1.100改为172.16.1.100,并将模式改为NAT,其他配置不变 virtual_server 172.16.1.100 80 { delay_loop 15 lb_algo rr lb_kind NAT #LVS工作模式 !persistence 60 protocol TCP ......
修改完之后重启服务
systemctl restart keepalived
LVS2修改的内容跟LVS1一样,修改完后重启服务(此处省略)
4.验证NAT+keepalived模式是否成功

关掉LVS1上的keepalived服务,再次验证,看keepalived有没有成功
systemctl stop keepalived
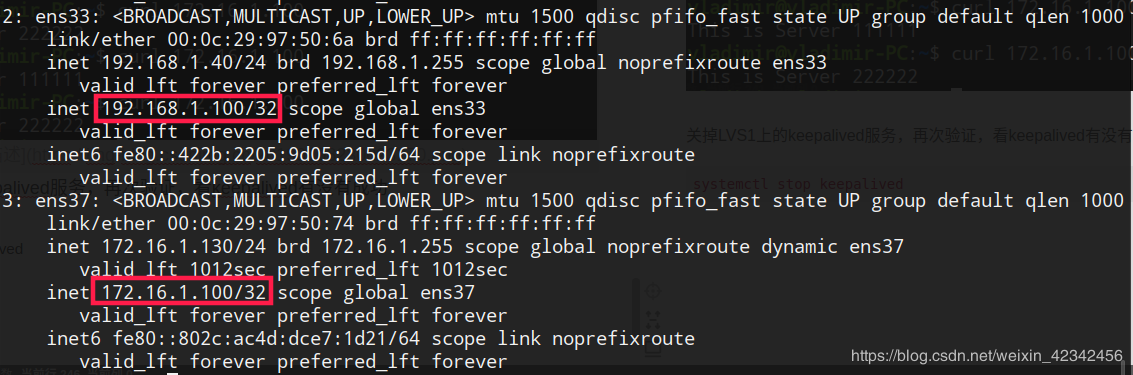
虚拟IP成功漂到备份服务器上
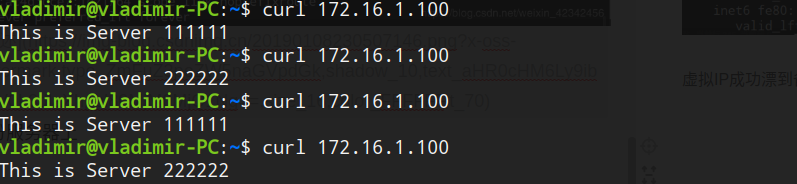
lvs负载正常跳转
————————————————
原文链接:https://blog.csdn.net/weixin_42342456/article/details/86100090
作者:陈耿聪 —— 夕狱
出处:https://www.cnblogs.com/CGCong/
本文版权归作者和博客园共有,欢迎转载,但未经作者同意必须保留此段声明,且在文章页面明显位置给出原文连接,否则保留追究法律责任的权利。





 浙公网安备 33010602011771号
浙公网安备 33010602011771号