一、简介
x509指令是一个功能很丰富的证书处理工具。可以用来显示证书的内容,转换其格式,给CSR签名等
二、语法
openssl x509 [-inform DER|PEM|NET] [-outform DER|PEM|NET] [-keyform DER|PEM] [-CAform DER|PEM] [-CAkeyform DER|PEM] [-in filename] [-out filename] [-passin arg] [-serial] [-hash] [-subject_hash] [-subject_hash_old] [-issuer_hash] [-issuer_hash_old] [-subject] [-issuer] [-nameopt option] [-email] [-ocspid] [-ocsp_uri] [-startdate] [-enddate] [-dates] [-purpose] [-modulus] [-fingerprint] [-alias] [-noout] [-trustout] [-clrtrust] [-clrreject] [-addtrust arg] [-addreject arg] [-setalias arg] [-days arg] [-checkend arg] [-set_serial n] [-signkey filename] [-x509toreq] [-req] [-CA filename] [-CAkey filename] [-CAcreateserial] [-CAserial filename] [-certopt] [-text] [-C] [-md2|-md5|-sha1|-mdc2] [-clrext] [-extfile filename] [-extensions section] [-engine id]
选项
-inform arg - input format - default PEM (one of DER, NET or PEM) -outform arg - output format - default PEM (one of DER, NET or PEM) -keyform arg - private key format - default PEM -CAform arg - CA format - default PEM -CAkeyform arg - CA key format - default PEM -in arg - input file - default stdin -out arg - output file - default stdout -passin arg - private key password source -serial - print serial number value -subject_hash - print subject hash value -subject_hash_old - print old-style (MD5) subject hash value -issuer_hash - print issuer hash value -issuer_hash_old - print old-style (MD5) issuer hash value -hash - synonym for -subject_hash -subject - print subject DN -issuer - print issuer DN -email - print email address(es) -startdate - notBefore field -enddate - notAfter field -purpose - print out certificate purposes -dates - both Before and After dates -modulus - print the RSA key modulus -pubkey - output the public key -fingerprint - print the certificate fingerprint -alias - output certificate alias -noout - no certificate output -ocspid - print OCSP hash values for the subject name and public key -ocsp_uri - print OCSP Responder URL(s) -trustout - output a "trusted" certificate -clrtrust - clear all trusted purposes -clrreject - clear all rejected purposes -addtrust arg - trust certificate for a given purpose -addreject arg - reject certificate for a given purpose -setalias arg - set certificate alias -days arg - How long till expiry of a signed certificate - def 30 days -checkend arg - check whether the cert expires in the next arg seconds exit 1 if so, 0 if not -signkey arg - self sign cert with arg -x509toreq - output a certification request object -req - input is a certificate request, sign and output. -CA arg - set the CA certificate, must be PEM format. -CAkey arg - set the CA key, must be PEM format missing, it is assumed to be in the CA file. -CAcreateserial - create serial number file if it does not exist -CAserial arg - serial file -set_serial - serial number to use -text - print the certificate in text form -C - print out C code forms -<dgst> - digest to use, see openssl dgst -h output for list -extfile - configuration file with X509V3 extensions to add -extensions - section from config file with X509V3 extensions to add -clrext - delete extensions before signing and input certificate -nameopt arg - various certificate name options -engine e - use engine e, possibly a hardware device. -certopt arg - various certificate text options
三、实例
1、生成自签名证书
openssl req -x509 -newkey rsa:1024 -keyout prikey.pem -passout pass:"123456" -new -out certself.pem
2、签发证书
签发v1格式证书
openssl x509 -req -in client_req.csr -CA certself.pem -CAkey prikey.pem -out client_cert.pem -CAcreateserial -days 365 -passin pass:"123456"
签发v3格式证书
openssl x509 -sha1 -req -in users.csr -CA caself.pem -CAkey cakey.pem -CAcreateserial -out users.pem -days 3650 -passin pass:11111111 -extfile /usr/share/ssl/openssl.cnf –extensions v3_req
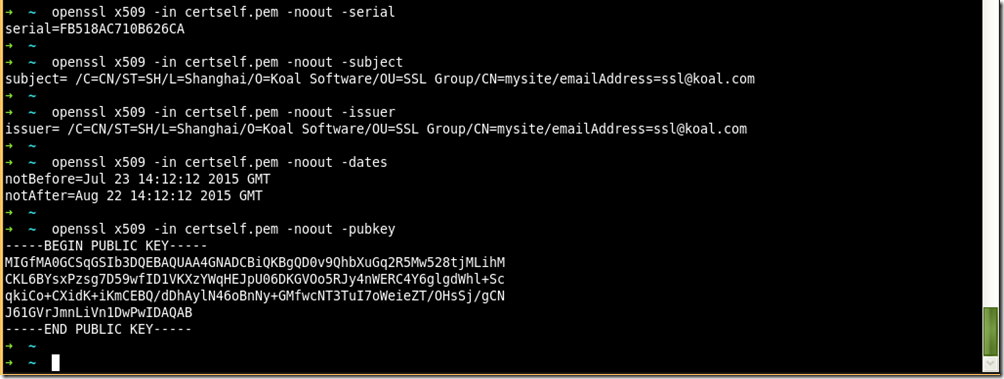
3、查看证书内容
openssl x509 -in cert.pem –noout -text
openssl x509 -in cert.pem –noout –srial
openssl x509 -in cert.pem –noout –subject
openssl x509 -in cert.pem –noout –issuer
openssl x509 -in cert.pem –noout –dates
openssl x509 -in cert.pem –noout –pubkey
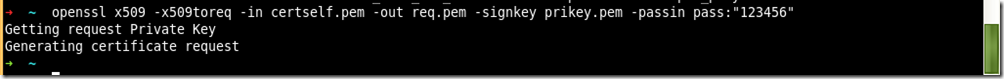
4、从证书中提取证书请求文件
openssl x509 -x509toreq -in certself.pem -out req.pem -signkey prikey.pem -passin pass:"123456"
5、从证书中提取公钥
openssl x509 -in certself.pem -pubkey -noout > pubkey2.pem




 浙公网安备 33010602011771号
浙公网安备 33010602011771号