20155222卢梓杰 实验四 恶意代码分析
实验四 恶意代码分析
1.系统运行监控
实验步骤如下
-
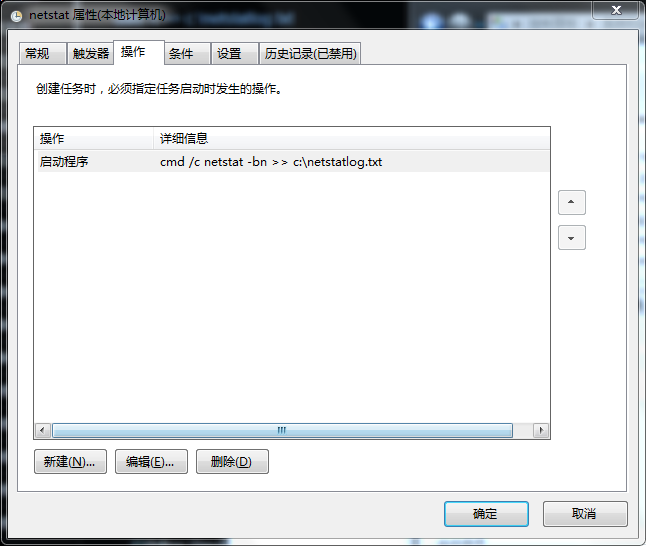
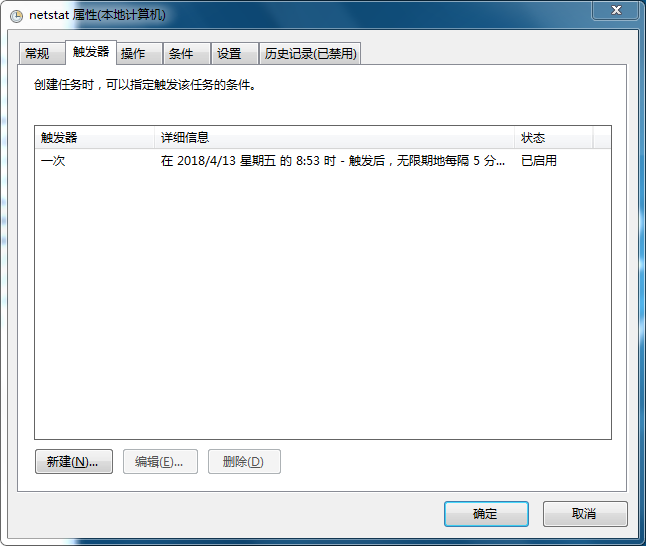
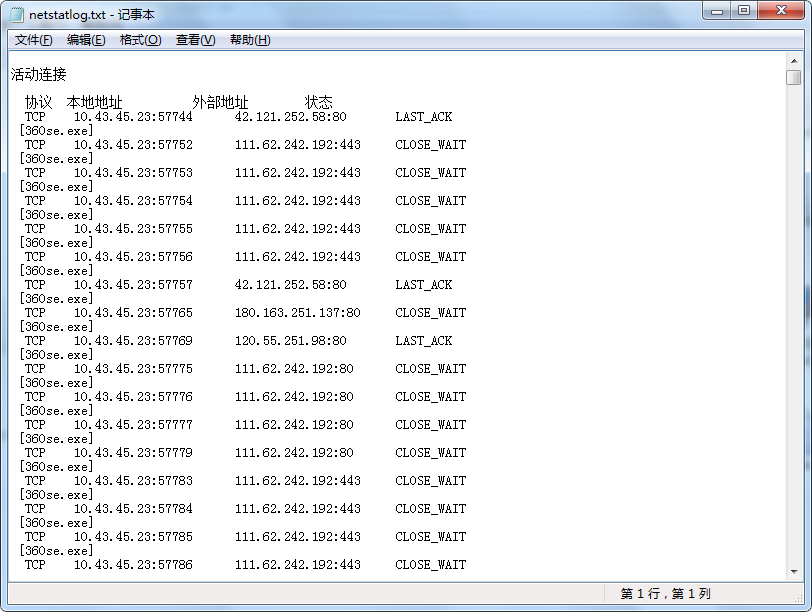
1.使用批处理监控程序连接网络的状况
在C盘要目录下建一个文件c:\netstatlog.bat,内容如下:date /t >> c:\netstatlog.txt time /t >> c:\netstatlog.txt netstat -bn >> c:\netstatlog.txt创建计划任务
C:\schtasks /create /TN netstat /sc MINUTE /MO 5 /TR "cmd /c netstat -bn >> c:\netstatlog.bat"![]()
![]()
![]()
一段时间后,开始分析产生的数据,尴尬的是不太会用excel,于是先用python对数据进行处理再导入到excel中f = open("C:\\netstatlog.txt") s = f.read() lines = s.split("\n") dict = {} for line in lines: if line.find("exe")>0: line = line[2:-1] if dict.get(line) == None: dict[line] = 1 else: dict[line] += 1 d = open("C:\\a.xls","w") for key in dict: result = key result += "\t" result += str(dict[key]) result += "\n" d.write(result) ``` 就成了这样。 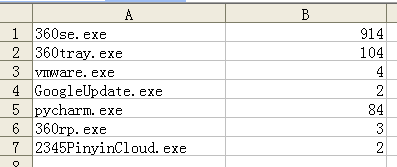 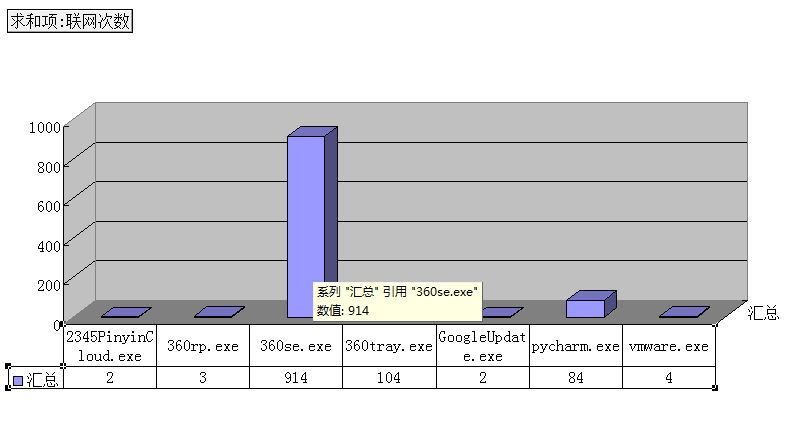 -
2.使用sysmon工具监控系统运行
- 1.修改配置文件
<Sysmon schemaversion="3.10"> <!-- Capture all hashes --> <HashAlgorithms>*</HashAlgorithms> <EventFiltering> <!-- Log all drivers except if the signature --> <!-- contains Microsoft or Windows --> <DriverLoad onmatch="exclude"> <Signature condition="contains">microsoft</Signature> <Signature condition="contains">windows</Signature> </DriverLoad> <NetworkConnect onmatch="exclude"> <Image condition="end with">chrome.exe</Image> <Image condition="end with">iexplorer.exe</Image> <SourcePort condition="is">137</SourcePort> <SourceIp condition="is">127.0.0.1</SourceIp> </NetworkConnect> <CreateRemoteThread onmatch="include"> <TargetImage condition="end with">explorer.exe</TargetImage> <TargetImage condition="end with">svchost.exe</TargetImage> <TargetImage condition="end with">winlogon.exe</TargetImage> <SourceImage condition="end with">powershell.exe</SourceImage> </CreateRemoteThread> </EventFiltering>
![]()
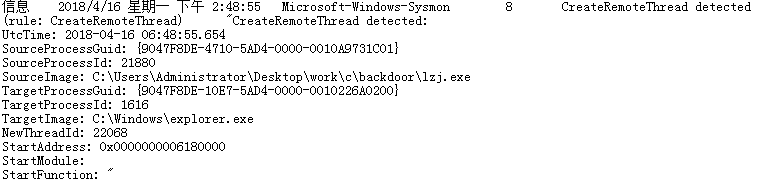
- 3.观测恶意程序
![]()
可以看出后门迁移到了explorer进程中
- 1.修改配置文件
-
3.Process Explorer
![]()






 浙公网安备 33010602011771号
浙公网安备 33010602011771号