代码审计-MKCMS任意密码重置漏洞
很简单的一个代码
/ucenter/repass.php
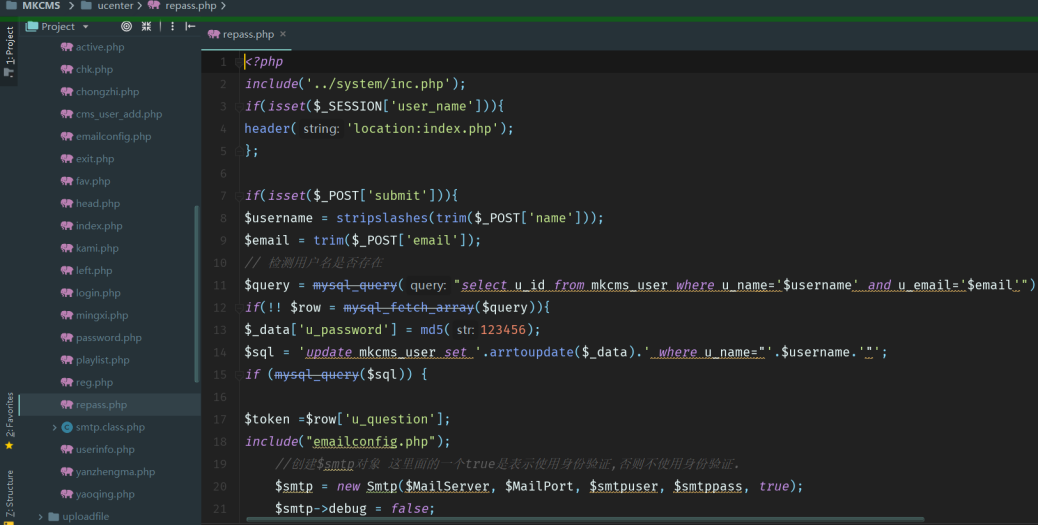
<?php
include('../system/inc.php');
if(isset($_SESSION['user_name'])){
header('location:index.php');
};
if(isset($_POST['submit'])){
$username = stripslashes(trim($_POST['name']));
$email = trim($_POST['email']);
// 检测用户名是否存在
$query = mysql_query("select u_id from mkcms_user where u_name='$username' and u_email='$email'");
if(!! $row = mysql_fetch_array($query)){
$_data['u_password'] = md5(123456);
$sql = 'update mkcms_user set '.arrtoupdate($_data).' where u_name="'.$username.'"';
if (mysql_query($sql)) {
$token =$row['u_question'];
include("emailconfig.php");
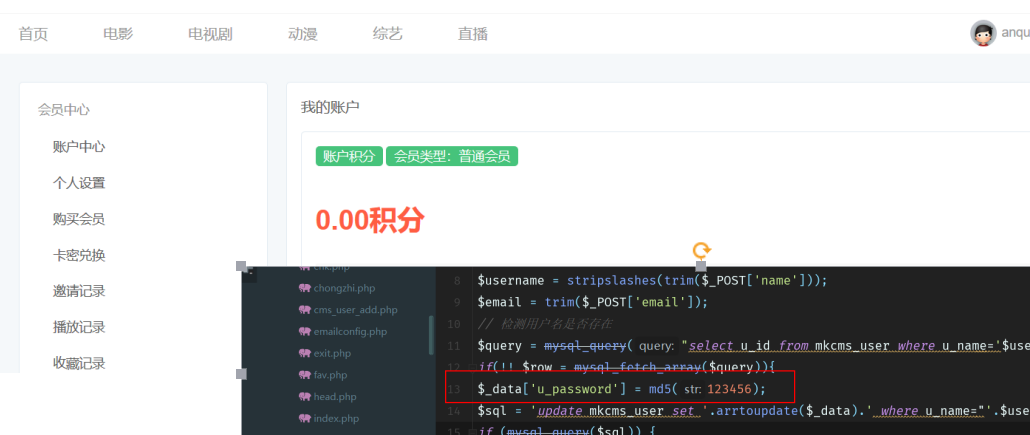
逻辑问题,程序未通过邮箱等验证是否为用户本身
然后在第13-14行用update语句把用户密码重置为123456了
静有所思,思有所想
------------------------------------------------------------------------------------
mail: 779783493@qq.com



 浙公网安备 33010602011771号
浙公网安备 33010602011771号