One cannot be in two places at once. Do you know what's "Dual Apps"? Manufactures like Xiaomi,Oppo,Huawei offer "Dual Apps" feature which allows users to run two different accounts of the same app on his/her phone. Let's take "Facebook" for example. The scenario is that a suspect's phone running Android 7 and we have to extract his/her "Facebook", including the original one and the clone one.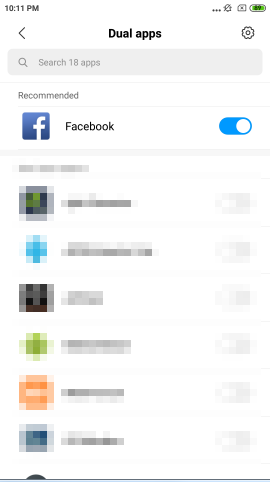
Now there are two Facebook Apps on suspect's phone. What's the clone one looks like? You could take a look as below. On the left side is the original one and the other side is the clone one.

Take a guess if you conduct "Downgrade Extraction" on suspect's phone to extract "Facebook", could you got both of these two "Facebook" without fail? The answer is "No". You only got the original one. So the question is: Where is the clone one and how to extract it? To achieve this, I borrow a rooted Xiaomi from a friend of mine and take a took. Very interesting there are two uid running the same app Facebook. u999? That's weird~
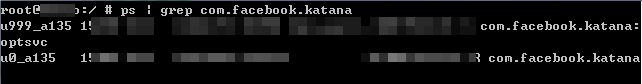
I've looked everywhere to search for the clone one facebook. I want to know exactly where it is. That's it. The path what I\m looking for is /data/user/999/ .
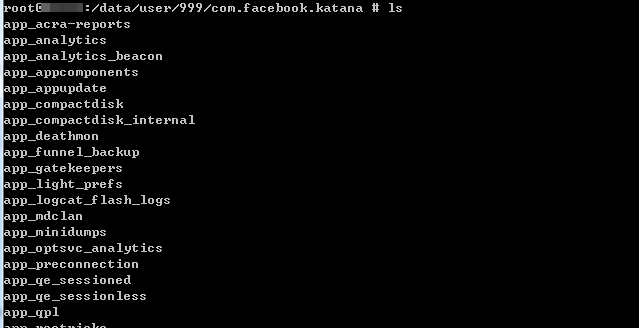
Of course the path may differ from brand to brand. Now "Downgrade Extraction" could extract the original one, but not working on the clone one. The challenge for Mobile forensic tools is to extract both "Dual Apps" on phones running Android 7 or above.




 浙公网安备 33010602011771号
浙公网安备 33010602011771号