Linux的一个问题ircbot进程
首先该问题目前还不清楚希望知道的人可以回复我mail fengtaotao2012x@163.com
今天执行一次常规服务器安全抽查的时候发现一台web服务器的一个奇怪的进程 而且更厉害的是cpu使用率高达百分之99
故事这样的 运行命令top
内容如下
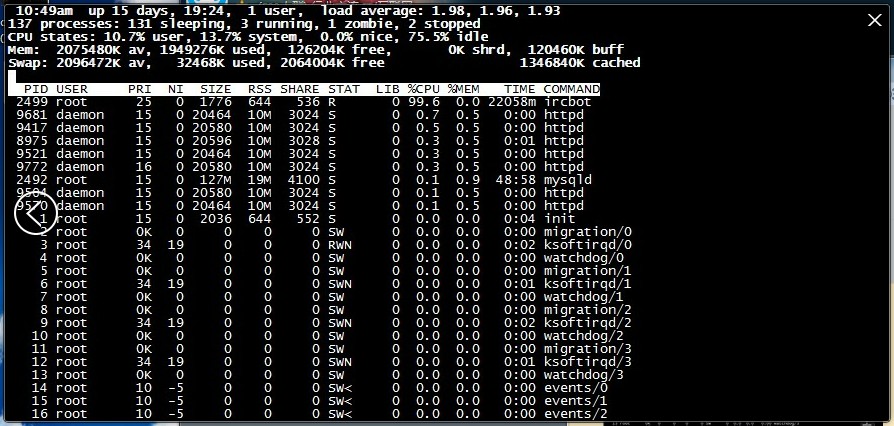
1 [root@mail log]# top 2 Unknown HZ value! (391) Assume 100. 3 4 11:25am up 15 days, 20:00, 2 users, load average: 1.76, 1.91, 1.97 5 139 processes: 133 sleeping, 1 running, 1 zombie, 4 stopped 6 CPU states: 1.3% user, 0.9% system, 0.0% nice, 97.7% idle 7 Mem: 2075480K av, 2000952K used, 74528K free, 0K shrd, 193716K buff 8 Swap: 2096472K av, 32464K used, 2064008K free 1296772K cached 9 10 PID USER PRI NI SIZE RSS SHARE STAT LIB %CPU %MEM TIME COMMAND 11 2499 root 25 0 1776 644 536 T 0 6.5 0.0 22094m ircbot 12 8975 daemon 15 0 20836 10M 3044 S 0 0.3 0.5 0:05 httpd 13 11465 daemon 15 0 21036 10M 3200 S 0 0.3 0.5 0:03 httpd 14 14287 daemon 15 0 20464 10M 2992 S 0 0.3 0.5 0:00 httpd 15 14304 daemon 15 0 20464 10M 2992 S 0 0.3 0.5 0:00 httpd 16 14305 daemon 15 0 20480 10M 2988 S 0 0.3 0.5 0:00 httpd 17 2492 root 15 0 127M 19M 4100 S 0 0.1 0.9 49:03 mysqld 18 12147 daemon 15 0 20792 10M 3024 S 0 0.1 0.5 0:02 httpd 19 12570 daemon 17 0 20568 10M 3008 S 0 0.1 0.5 0:02 httpd 20 14307 daemon 15 0 20448 10M 2992 S 0 0.1 0.5 0:00 httpd 21 14317 daemon 17 0 20448 10M 2972 S 0 0.1 0.4 0:00 httpd 22 1 root 15 0 2036 644 552 S 0 0.0 0.0 0:04 init 23 2 root 0K 0 0 0 0 SW 0 0.0 0.0 0:00 migration/0 24 3 root 34 19 0 0 0 SWN 0 0.0 0.0 0:02 ksoftirqd/0 25 4 root 0K 0 0 0 0 SW 0 0.0 0.0 0:00 watchdog/0 26 5 root 0K 0 0 0 0 SW 0 0.0 0.0 0:00 migration/1 27 6 root 34 19 0 0 0 SWN 0 0.0 0.0 0:01 ksoftirqd/1 28 7 root 0K 0 0 0 0 SW 0 0.0 0.0 0:00 watchdog/1 29 8 root 0K 0 0 0 0 SW 0 0.0 0.0 0:00 migration/2 30 9 root 34 19 0 0 0 SWN 0 0.0 0.0 0:02 ksoftirqd/2 31 10 root 0K 0 0 0 0 SW 0 0.0 0.0 0:00 watchdog/2 32 11 root 0K 0 0 0 0 SW 0 0.0 0.0 0:00 migration/3
当我看到第一行的时候第一感觉就是病毒- -!
1 [root@mail log]# top 2 Unknown HZ value! (391) Assume 100. 3 4 11:25am up 15 days, 20:00, 2 users, load average: 1.76, 1.91, 1.97 5 139 processes: 133 sleeping, 1 running, 1 zombie, 4 stopped 6 CPU states: 1.3% user, 0.9% system, 0.0% nice, 97.7% idle 7 Mem: 2075480K av, 2000952K used, 74528K free, 0K shrd, 193716K buff 8 Swap: 2096472K av, 32464K used, 2064008K free 1296772K cached 9 10 PID USER PRI NI SIZE RSS SHARE STAT LIB %CPU %MEM TIME COMMAND 11 2499 root 25 0 1776 644 536 T 0 6.5 0.0 22094m ircbot
这样的数据太吓人了 好吧根据id找下程序的位置
运行:
1 [root@mail log]# ls -l /proc/2499/ 2 total 0 3 dr-xr-xr-x 2 root root 0 Jun 19 11:47 attr 4 -r-------- 1 root root 0 Jun 19 11:47 auxv 5 -r--r--r-- 1 root root 0 Jun 17 04:02 cmdline 6 -r--r--r-- 1 root root 0 Jun 19 11:47 cpuset 7 lrwxrwxrwx 1 root root 0 Jun 19 11:47 cwd -> / 8 -r-------- 1 root root 0 Jun 19 11:12 environ 9 lrwxrwxrwx 1 root root 0 Jun 19 11:47 exe -> /usr/share/icbm/ircbot 10 dr-x------ 2 root root 0 Jun 19 11:47 fd 11 -rw-r--r-- 1 root root 0 Jun 19 11:47 loginuid 12 -r-------- 1 root root 0 Jun 19 11:47 maps 13 -rw------- 1 root root 0 Jun 19 11:47 mem 14 -r--r--r-- 1 root root 0 Jun 19 11:47 mounts 15 -r-------- 1 root root 0 Jun 19 11:47 mountstats 16 -rw-r--r-- 1 root root 0 Jun 19 11:47 oom_adj 17 -r--r--r-- 1 root root 0 Jun 19 11:47 oom_score 18 lrwxrwxrwx 1 root root 0 Jun 19 11:47 root -> / 19 -r--r--r-- 1 root root 0 Jun 19 11:47 schedstat 20 -r-------- 1 root root 0 Jun 19 11:47 smaps 21 -r--r--r-- 1 root root 0 Jun 17 04:02 stat 22 -r--r--r-- 1 root root 0 Jun 19 10:47 statm 23 -r--r--r-- 1 root root 0 Jun 19 11:12 status 24 dr-xr-xr-x 3 root root 0 Jun 19 11:47 task 25 -r--r--r-- 1 root root 0 Jun 19 11:47 wchan
ls -l /proc/2499/ext
1 [root@mail log]# ls -l /proc/2499/exe 2 audit/ conman.old/ httpd/ messages.1 secure.1 spooler.4 3 boot.log cron lastlog messages.2 secure.2 squid/ 4 boot.log.1 cron.1 mail/ messages.3 secure.3 vbox/ 5 boot.log.2 cron.2 maillog messages.4 secure.4 wtmp 6 boot.log.3 cron.3 maillog.1 mysqld.log setroubleshoot/ wtmp.1 7 boot.log.4 cron.4 maillog.2 ppp/ spooler xferlog 8 boot.log.bak cups/ maillog.3 prelink/ spooler.1 yum.log 9 clamav/ dmesg maillog.4 samba/ spooler.2 10 conman/ gdm/ messages secure spooler.3
1 [root@mail log]# ls -l /proc/2499/exe 2 lrwxrwxrwx 1 root root 0 Jun 19 11:47 /proc/2499/exe -> /usr/share/icbm/ircbot
这里说明下exe为一个快捷方式Linux为软连接方法为:ln -s xxx xxx 上述的意思为 2499的进程目录会跳转到 /usr/share/icbm/ircbot
想打开这个文件看下内容不过发现打开的是乱码,cp下来在windows下很多编程工具软件也是打开乱码,可能是动了手脚
这个是我cp下来的目录http://pan.baidu.com/share/link?shareid=2265703552&uk=4045574093 有兴趣的可以看下
1 [root@mail ~]# ll -d /usr/share/icbm/ 2 drwxr-xr-x 2 root root 4096 Apr 8 06:27 /usr/share/icbm/ 3 [root@mail ~]# ll /usr/share/icbm/* 4 -rwxrwxrwx 1 root root 1005 Jul 27 2012 /usr/share/icbm/flood.pl 5 -rwxrwxrwx 1 root root 135 Dec 14 2010 /usr/share/icbm/geekymedia.repo 6 -rwxrwxrwx 1 root root 1384 Oct 27 2012 /usr/share/icbm/getproxies.php 7 -rwxr-xr-x 1 root root 27788 Apr 8 01:09 /usr/share/icbm/ircbot 8 -rwxrwxrwx 1 root root 204562 Apr 7 09:40 /usr/share/icbm/proxies.txt 9 -rwxrwxrwx 1 root root 12700 Sep 18 2012 /usr/share/icbm/rpmforge.rpm 10 -rwxrwxrwx 1 root root 17072 Apr 12 2012 /usr/share/icbm/slowloris.pl 11 -rwxrwxrwx 1 root root 11087 Oct 26 2012 /usr/share/icbm/syn.pl 12 -rwxrwxrwx 1 root root 699 Jul 27 2012 /usr/share/icbm/udp.py 13 [root@mail ~]#
发现的问题是 这里面只有
7 -rwxr-xr-x 1 root root 27788 Apr 8 01:09 /usr/share/icbm/ircbot 8 -rwxrwxrwx 1 root root 204562 Apr 7 09:40 /usr/share/icbm/proxies.txt
这两个是在今年的4月份先后出现的。
目前也只能先将其rm -f掉了,当然我有beckup
等待网友们的热心支援! 问了几个老运维说 入侵以后最好是把资料CP出来然后重做系统,但我不想那样,希望找到一个优的方法。
删除掉以后 reboot了下 开机半小时 使用top 命令查看服务器的进程稳定下来了,而且 free -m查看 swap的使用为0了
1 1:48pm up 3 min, 1 user, load average: 0.33, 0.31, 0.13 2 105 processes: 103 sleeping, 2 running, 0 zombie, 0 stopped 3 CPU states: 0.7% user, 0.0% system, 0.0% nice, 99.2% idle 4 Mem: 2075480K av, 665456K used, 1410024K free, 0K shrd, 16496K buff 5 Swap: 2096472K av, 0K used, 2096472K free 297804K cached 6 7 PID USER PRI NI SIZE RSS SHARE STAT LIB %CPU %MEM TIME COMMAND 8 2592 daemon 15 0 20792 10M 3020 S 0 0.3 0.5 0:00 httpd 9 2701 daemon 15 0 20464 10M 2992 S 0 0.3 0.5 0:00 httpd 10 2711 daemon 15 0 20448 10M 2992 S 0 0.3 0.5 0:00 httpd 11 2712 daemon 16 0 20980 10M 3004 R 0 0.3 0.5 0:00 httpd 12 2729 daemon 15 0 20464 10M 2992 S 0 0.3 0.5 0:00 httpd 13 2511 root 15 0 124M 16M 3640 S 0 0.1 0.8 0:00 mysqld 14 2588 daemon 15 0 20804 10M 3008 S 0 0.1 0.5 0:00 httpd 15 2590 daemon 15 0 20804 10M 3012 S 0 0.1 0.5 0:00 httpd 16 2591 daemon 15 0 20464 10M 3008 S 0 0.1 0.5 0:00 httpd 17 2703 daemon 15 0 20464 10M 3024 S 0 0.1 0.5 0:00 httpd 18 2714 daemon 17 0 20464 10M 3000 S 0 0.1 0.5 0:00 httpd 19 3058 root 15 0 2940 1840 1632 R 0 0.1 0.0 0:00 top 20 1 root 15 0 2036 644 552 S 0 0.0 0.0 0:01 init 21 2 root 0K 0 0 0 0 SW 0 0.0 0.0 0:00 migration/0 22 3 root 34 19 0 0 0 SWN 0 0.0 0.0 0:00 ksoftirqd/0 23 4 root 0K 0 0 0 0 SW 0 0.0 0.0 0:00 watchdog/0 24 5 root 0K 0 0 0 0 SW 0 0.0 0.0 0:00 migration/1 25 6 root 34 19 0 0 0 SWN 0 0.0 0.0 0:00 ksoftirqd/1 26 7 root 0K 0 0 0 0 SW 0 0.0 0.0 0:00 watchdog/1 27 8 root 0K 0 0 0 0 SW 0 0.0 0.0 0:00 migration/2 28 9 root 39 19 0 0 0 SWN 0 0.0 0.0 0:00 ksoftirqd/2 29 10 root 0K 0 0 0 0 SW 0 0.0 0.0 0:00 watchdog/2 30 11 root 0K 0 0 0 0 SW 0 0.0 0.0 0:00 migration/3 31 12 root 34 19 0 0 0 SWN 0 0.0 0.0 0:00 ksoftirqd/3 32 13 root 0K 0 0 0 0 SW 0 0.0 0.0 0:00 watchdog/3 33 [root@mail ~]# free -m 34 total used free shared buffers cached 35 Mem: 2026 649 1377 0 16 290 36 -/+ buffers/cache: 342 1684 37 Swap: 2047 0 2047
在使用 top -p 2499 没有了。
不过还是很担心 因为怕病毒修改了系统的bin文件 哎还是精简测下这几天的服务器吧!
到目前为止的检测还算正常



