服务器是否被入侵的排查方案
- 背景
随着开源产品的越来越盛行,作为网络安全从业者,能够清晰地鉴别异常机器是否已经被入侵了显得至关重要,个人结合自己的工作经历,整理了几种常见的机器被入侵情况供参考
- 日志信息
入侵者可能会删除机器的日志信息,可以查看日志信息是否还存在或者是否被清空,相关命令示例:
点击查看代码
[root@localhost ~]# ll -h /var/log/*
-rw-------. 1 root root 0 Nov 18 00:01 /var/log/boot.log
-rw-------. 1 root root 36K Nov 18 00:01 /var/log/boot.log-20221118
-rw-rw----. 1 root utmp 0 Dec 1 00:01 /var/log/btmp
-rw-rw----. 1 root utmp 2.7K Nov 16 10:19 /var/log/btmp-20221201
-rw-------. 1 root root 38K Dec 15 08:01 /var/log/cron
-rw-------. 1 root root 31K Nov 19 23:01 /var/log/cron-20221120
-rw-------. 1 root root 60K Nov 26 23:01 /var/log/cron-20221127
-rw-------. 1 root root 60K Dec 3 23:01 /var/log/cron-20221204
-rw-------. 1 root root 60K Dec 10 23:01 /var/log/cron-20221211
-rw-r--r--. 1 root root 239K Dec 15 07:43 /var/log/dnf.librepo.log
[root@localhost ~]# du -sh /var/log/*
6.3M /var/log/anaconda
1.1M /var/log/audit
0 /var/log/boot.log
36K /var/log/boot.log-20221118
0 /var/log/btmp
4.0K /var/log/btmp-20221201
0 /var/log/chrony
40K /var/log/cron
32K /var/log/cron-20221120
2.新建用户名和密码文件
入侵者可能创建一个新的存放用户名及密码文件,可以查看/etc/passwd及/etc/shadow文件,相关命令示例:
点击查看代码
[root@localhost ~]# ll /etc/pass*
-rw-r--r--. 1 root root 2473 Nov 17 10:54 /etc/passwd
-rw-r--r--. 1 root root 2411 Nov 16 11:10 /etc/passwd-
[root@localhost ~]# ll /etc/sha*
----------. 1 root root 1208 Nov 17 10:54 /etc/shadow
----------. 1 root root 1189 Nov 16 11:10 /etc/shadow-
点击查看代码
[root@localhost ~]# more /etc/passwd
root:x:0:0:root:/root:/bin/bash
bin:x:1:1:bin:/bin:/sbin/nologin
daemon:x:2:2:daemon:/sbin:/sbin/nologin
adm:x:3:4:adm:/var/adm:/sbin/nologin
lp:x:4:7:lp:/var/spool/lpd:/sbin/nologin
sync:x:5:0:sync:/sbin:/bin/sync
shutdown:x:6:0:shutdown:/sbin:/sbin/shutdown
halt:x:7:0:halt:/sbin:/sbin/halt
点击查看代码
[root@localhost ~]# lastlog
Username Port From Latest
root pts/0 10.65.30.83 Wed Dec 14 21:12:58 +0800 2022
bin **Never logged in**
daemon **Never logged in**
adm **Never logged in**
lp **Never logged in**
sync **Never logged in**
shutdown **Never logged in**
halt **Never logged in**
mail **Never logged in**
operator **Never logged in**
games **Never logged in**
ftp **Never logged in**
nobody **Never logged in**
tss **Never logged in**
unbound **Never logged in**
systemd-coredump **Never logged in**
dbus **Never logged in**
polkitd **Never logged in**
点击查看代码
[root@localhost ~]# who
root pts/0 2022-12-14 21:12 (10.65.30.83)
点击查看代码
[root@localhost ~]# last
root pts/0 10.65.30.83 Wed Dec 14 21:12 still logged in
root pts/0 10.65.30.83 Wed Dec 14 17:23 - 21:12 (03:49)
root pts/0 10.65.30.83 Wed Dec 14 11:25 - 16:57 (05:31)
root pts/0 10.65.30.83 Wed Dec 14 10:47 - 11:21 (00:33)
root pts/0 10.65.30.83 Wed Dec 14 10:08 - 10:13 (00:05)
root pts/1 10.65.30.83 Wed Dec 14 10:01 - 10:01 (00:00)
root pts/0 10.65.30.83 Wed Dec 14 10:01 - 10:01 (00:00)
root pts/2 10.65.30.83 Thu Nov 17 11:44 - 16:24 (1+04:40)
root pts/2 10.65.30.83 Thu Nov 17 11:44 - 11:44 (00:00)
root pts/2 10.65.30.83 Thu Nov 17 11:39 - 11:44 (00:04)
root pts/2 10.65.30.83 Thu Nov 17 11:34 - 11:36 (00:01)
root pts/1 10.65.30.83 Wed Nov 16 11:58 - 16:24 (2+04:26)
root pts/1 10.65.30.83 Wed Nov 16 11:58 - 11:58 (00:00)
root pts/1 10.65.30.83 Wed Nov 16 11:05 - 11:48 (00:43)
root pts/0 10.65.30.83 Wed Nov 16 10:43 - 16:55 (2+06:11)
root pts/0 10.65.30.83 Wed Nov 16 10:35 - 10:36 (00:00)
reboot system boot 5.14.0-160.el9.x Wed Nov 16 10:35 still running
点击查看代码
[root@localhost ~]# ac -dp
root 26.29
llz 0.48
Nov 16 total 26.77
root 60.36
Nov 17 total 60.36
root 49.76
Nov 18 total 49.76
root 12.80
Dec 14 total 12.80
root 9.14
Today total 9.14
点击查看代码
[root@localhost ~]# cat /var/log/secure
Dec 14 10:01:07 localhost sshd[92287]: Accepted password for root from 10.65.30.83 port 3198 ssh2
Dec 14 10:01:07 localhost systemd[92307]: pam_unix(systemd-user:session): session opened for user root(uid=0) by (uid=0)
Dec 14 10:01:07 localhost sshd[92287]: pam_unix(sshd:session): session opened for user root(uid=0) by (uid=0)
Dec 14 10:01:07 localhost sshd[92303]: Accepted password for root from 10.65.30.83 port 3321 ssh2
Dec 14 10:01:08 localhost sshd[92303]: pam_unix(sshd:session): session opened for user root(uid=0) by (uid=0)
Dec 14 10:01:25 localhost sshd[92433]: Accepted password for root from 10.65.30.83 port 3392 ssh2
Dec 14 10:01:25 localhost sshd[92433]: pam_unix(sshd:session): session opened for user root(uid=0) by (uid=0)
Dec 14 10:01:25 localhost sshd[92437]: Accepted password for root from 10.65.30.83 port 3397 ssh2
Dec 14 10:01:25 localhost sshd[92437]: pam_unix(sshd:session): session opened for user root(uid=0) by (uid=0)
Dec 14 10:01:27 localhost sshd[92433]: pam_unix(sshd:session): session closed for user root
Dec 14 10:01:28 localhost sshd[92437]: pam_unix(sshd:session): session closed for user root
Dec 14 10:01:28 localhost sshd[92287]: pam_unix(sshd:session): session closed for user root
Dec 14 10:01:29 localhost sshd[92303]: pam_unix(sshd:session): session closed for user root
10.异常进程树
查询异常进程所对应的执行脚本文件
10. 1
top命令查看异常进程对应的PID
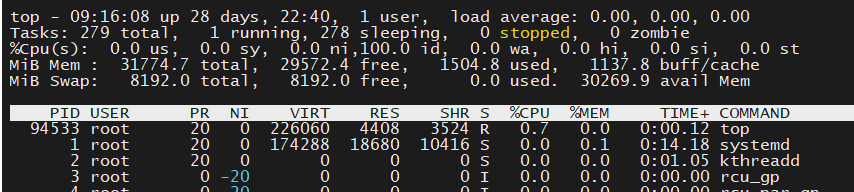
10. 2 在虚拟文件系统目录查找该进程的可执行文件
点击查看代码
[root@localhost ~]# ll /proc/1429/ | grep -i exe
lrwxrwxrwx. 1 gdm gdm 0 Nov 16 10:35 exe -> /usr/bin/gnome-shell
[root@localhost ~]# ll /usr/bin/gnome-shell
-rwxr-xr-x. 1 root root 24784 Oct 15 18:30 /usr/bin/gnome-shell
点击查看代码
1.查看/var/log/secure文件,发现已经没有该文件
[root@localhost ~]# ll /var/log/secure
ls: cannot access '/var/log/secure': No such file or directory
2.使用lsof命令查看当前是否有进程打开/var/log/secure,
[root@localhost ~]# lsof | grep /var/log/secure
rsyslogd 944 root 9w REG 253,0 4742 136140001 /var/log/secure (deleted)
rsyslogd 944 962 in:imjour root 9w REG 253,0 4742 136140001 /var/log/secure (deleted)
rsyslogd 944 963 rs:main root 9w REG 253,0 4742 136140001 /var/log/secure (deleted)
3.从上面的信息可以看到 PID 944(rsyslogd)打开文件的文件描述符,同时还可以看到/var/log/ secure已经标记为被删除了。因此我们可以在/proc/944/fd/9(fd下的每个以数字命名的文件表示进程对应的文件描述符)中查看相应的信息,如下:
[root@localhost ~]# tail /proc/944/fd/9
Dec 14 17:23:39 localhost sshd[93442]: pam_unix(sshd:session): session opened for user root(uid=0) by (uid=0)
Dec 14 17:23:40 localhost sshd[93449]: Accepted password for root from 10.65.30.83 port 5669 ssh2
Dec 14 17:23:40 localhost sshd[93449]: pam_unix(sshd:session): session opened for user root(uid=0) by (uid=0)
Dec 14 21:12:44 localhost sshd[93442]: pam_unix(sshd:session): session closed for user root
Dec 14 21:12:44 localhost sshd[93449]: pam_unix(sshd:session): session closed for user root
Dec 14 21:12:58 localhost sshd[93771]: Accepted password for root from 10.65.30.83 port 8071 ssh2
Dec 14 21:12:58 localhost systemd[93779]: pam_unix(systemd-user:session): session opened for user root(uid=0) by (uid=0)
Dec 14 21:12:58 localhost sshd[93771]: pam_unix(sshd:session): session opened for user root(uid=0) by (uid=0)
Dec 14 21:12:58 localhost sshd[93776]: Accepted password for root from 10.65.30.83 port 8074 ssh2
Dec 14 21:12:58 localhost sshd[93776]: pam_unix(sshd:session): session opened for user root(uid=0) by (uid=0)
4.从上面的信息可以看出,查看/proc/1264/fd/4就可以得到所要恢复的数据。如果可以通过文件描述符查看相应的数据,那么就可以使用I/O重定向将其重定向到文件中,如:
[root@localhost ~]# cat /proc/944/fd/9 > /var/log/secure
5.再次查看/var/log/secure,发现该文件已经存在。对于许多应用程序,尤其是日志文件和数据库,这种恢复删除文件的方法非常有用。

 浙公网安备 33010602011771号
浙公网安备 33010602011771号