linux系统中iptables防火墙管理工具
策略以规则链:
防火墙会从上至下的顺序来读取配置的策略规则,在找到匹配项后就立即结束匹配工作并去执行匹配项中定义的行为(即方形或者阻止)如果在读取完所有的策略规则之后没有匹配项,就去执行默认的策略。
一般而言,防火墙策略规则的设置有两种:一种是“通”(即放行),一种是“堵”(即阻止)。
iptables服务把用于处理或过滤流量的策略条目称之为规则,多条规则可以组成一个规则链,而规则链则依据数据包处理位置的不同进行分类,具体如下:
在进行路由选择前处理数据包(PREROUTING)
处理流入的数据包(INPUT)
处理流出的数据包(OUTPUT)
处理转发的数据包(FORWARD)
在进行路由选择后处理数据包(POSTROUTING)
一般来说,从内网向外网发送的流量一般都是可控且良性的,因此我们使用最多的就是INOUT规则链,该规则链可以增大黑客人员从外网入侵内网的难度。
iptables中基本的命令参数:
iptables是一款基于命令行的防火墙策略管理工具。iptables命令可以根据流量的源地址、目的地址、传输协议、服务类型等信息进行匹配,一旦匹配成功,iptables就会根据策略规则所预设的动作来吃力这些流量。
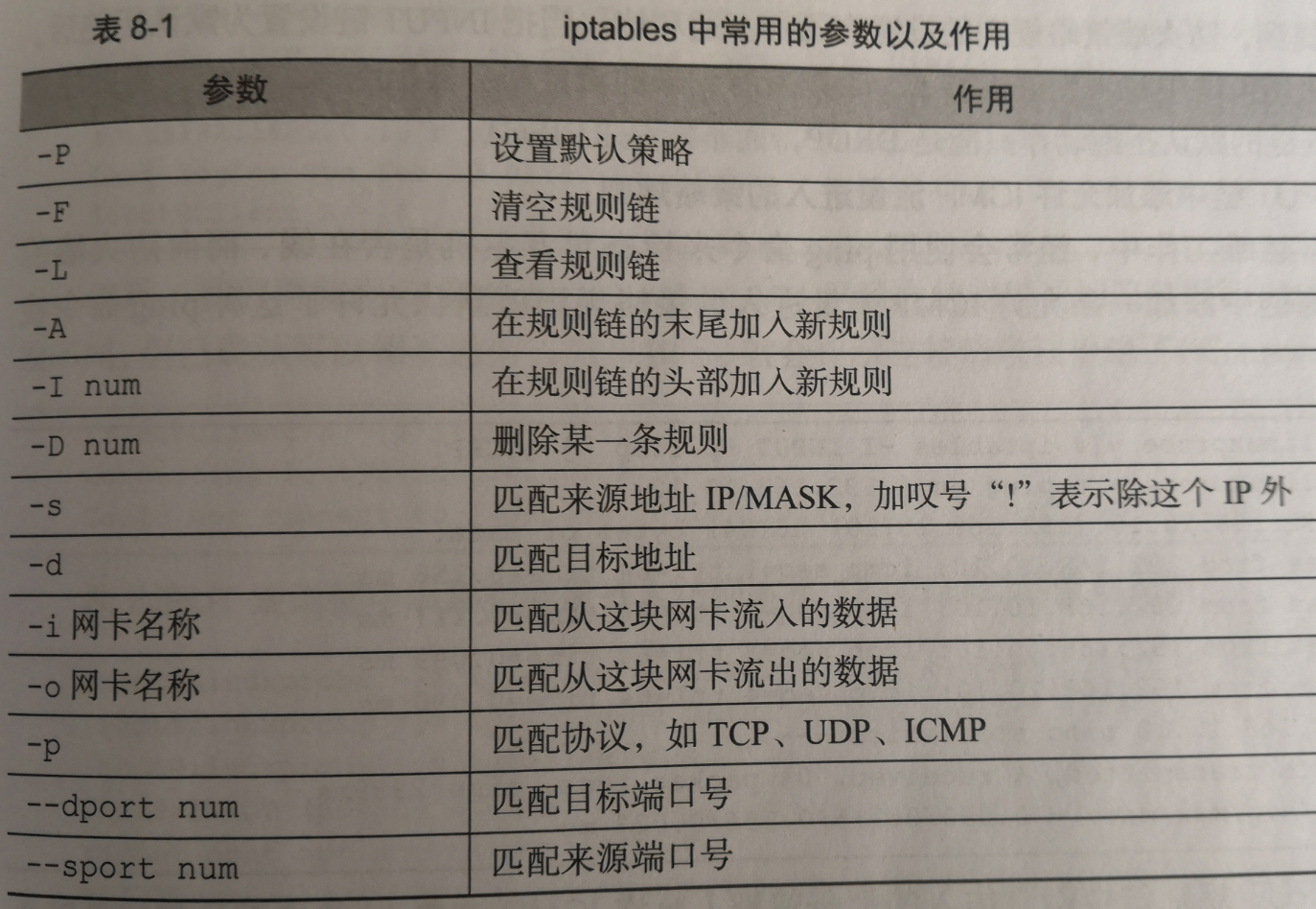
防火墙策略规则的匹配顺序是从上至下的 ,因此要把较为严格、优先级较高的策略规则放在前面。iptables中常用的参数及作用见下图:
1、在iptables命令后加-L参数查看已有的防火墙规则链:
[root@linuxprobe /]# iptables -L | wc -l ## 统计行数
104
[root@linuxprobe /]# iptables -L | head ## 查看前十行
Chain INPUT (policy ACCEPT)
target prot opt source destination
ACCEPT all -- anywhere anywhere ctstate RELATED,ESTABLISHED
ACCEPT all -- anywhere anywhere
INPUT_direct all -- anywhere anywhere
INPUT_ZONES_SOURCE all -- anywhere anywhere
INPUT_ZONES all -- anywhere anywhere
ACCEPT icmp -- anywhere anywhere
REJECT all -- anywhere anywhere reject-with icmp-host-prohibited
[root@linuxprobe /]# iptables -L | tail
ACCEPT tcp -- anywhere anywhere tcp dpt:ssh ctstate NEW
Chain IN_public_deny (1 references)
target prot opt source destination
Chain IN_public_log (1 references)
target prot opt source destination
Chain OUTPUT_direct (1 references)
target prot opt source destination
2、在iptables命令后添加-F参数清空已有的防火墙规则链:
[root@linuxprobe /]# iptables -F ## 清空已有的防火墙规则链
[root@linuxprobe /]# iptables -L | wc -l ## 统计行数
71
[root@linuxprobe /]# iptables -L | head ## 查看前十行
Chain INPUT (policy ACCEPT)
target prot opt source destination
Chain FORWARD (policy ACCEPT)
target prot opt source destination
Chain OUTPUT (policy ACCEPT)
target prot opt source destination
Chain FORWARD_IN_ZONES (0 references)
[root@linuxprobe /]# iptables -L | tail
target prot opt source destination
Chain IN_public_deny (0 references)
target prot opt source destination
Chain IN_public_log (0 references)
target prot opt source destination
Chain OUTPUT_direct (0 references)
target prot opt source destination
3、把INPUT规则链的默认策略设置为拒绝:
[root@linuxprobe /]# iptables -L | head ## 查看设置前为ACCEPT
Chain INPUT (policy ACCEPT)
target prot opt source destination
Chain FORWARD (policy ACCEPT)
target prot opt source destination
Chain OUTPUT (policy ACCEPT)
target prot opt source destination
Chain FORWARD_IN_ZONES (0 references)
[root@linuxprobe /]# iptables -P INPUT DROP ## 把INPUT规则链的默认策略设置为拒绝,-P表示设置默认策略
[root@linuxprobe ~]# iptables -L | head ## 查看
Chain INPUT (policy DROP)
target prot opt source destination
Chain FORWARD (policy ACCEPT)
target prot opt source destination
Chain OUTPUT (policy ACCEPT)
target prot opt source destination
Chain FORWARD_IN_ZONES (0 references)
当防火墙的默认策略为拒绝时,就要设置允许规则,否则谁都进不来;如果防火墙的默认策略为允许时,就要设置拒绝规则,否则谁都能进来,防火墙也就失去了防范的作用。
另外,规则链默认拒绝动作只能是DROP,而不能是REJ ECT。
4、向INPUT链中添加允许ICMP流量进入的策略规则:
[root@linuxprobe ~]# iptables -L | head ## 查看修改前防火墙规则链
Chain INPUT (policy DROP)
target prot opt source destination
Chain FORWARD (policy ACCEPT)
target prot opt source destination
Chain OUTPUT (policy ACCEPT)
target prot opt source destination
Chain FORWARD_IN_ZONES (0 references)
[root@linuxprobe ~]# ifconfig | head ## 查看本机IP
eno16777728: flags=4163<UP,BROADCAST,RUNNING,MULTICAST> mtu 1500
inet 192.168.3.13 netmask 255.255.255.0 broadcast 192.168.3.255
inet6 fe80::20c:29ff:feab:7b00 prefixlen 64 scopeid 0x20<link>
ether 00:0c:29:ab:7b:00 txqueuelen 1000 (Ethernet)
RX packets 845 bytes 79101 (77.2 KiB)
RX errors 0 dropped 0 overruns 0 frame 0
TX packets 576 bytes 81095 (79.1 KiB)
TX errors 0 dropped 0 overruns 0 carrier 0 collisions 0
lo: flags=73<UP,LOOPBACK,RUNNING> mtu 65536
[root@linuxprobe ~]# ping -c 4 192.168.3.13 ## 测试连通性
PING 192.168.3.13 (192.168.3.13) 56(84) bytes of data.
--- 192.168.3.13 ping statistics ---
4 packets transmitted, 0 received, 100% packet loss, time 2999ms
[root@linuxprobe ~]# iptables -I INPUT -p icmp -j ACCEPT ## 允许icmp流量进入,-I 表示在规则链头部胶乳新规则,-p表示匹配协议,如TCP、UDP、ICMP等,-j??
[root@linuxprobe ~]# ping -c 4 192.168.3.13 ## 测试连通性
PING 192.168.3.13 (192.168.3.13) 56(84) bytes of data.
64 bytes from 192.168.3.13: icmp_seq=1 ttl=64 time=0.075 ms
64 bytes from 192.168.3.13: icmp_seq=2 ttl=64 time=0.041 ms
64 bytes from 192.168.3.13: icmp_seq=3 ttl=64 time=0.040 ms
64 bytes from 192.168.3.13: icmp_seq=4 ttl=64 time=0.037 ms
--- 192.168.3.13 ping statistics ---
4 packets transmitted, 4 received, 0% packet loss, time 2999ms
rtt min/avg/max/mdev = 0.037/0.048/0.075/0.016 ms
[root@linuxprobe ~]# iptables -L | head ## 查看修改后防火墙规则链
Chain INPUT (policy DROP)
target prot opt source destination
ACCEPT icmp -- anywhere anywhere
Chain FORWARD (policy ACCEPT)
target prot opt source destination
Chain OUTPUT (policy ACCEPT)
target prot opt source destination
注:
a、TCP是一种面向连bai接的、可靠的、基于字节流的传输层通信协议,由IETF的RFC 793定义。在简化的计算机网络OSI模型中,它完成第四层传输层所指定的功能。在因特网协议族中,TCP层是位于IP层之上,应用层之下的中间层。不同主机的应用层之间经常需要可靠的、像管道一样的连接,但是IP层不提供这样的流机制,而是提供不可靠的包交换。
b、UDP 是User Datagram Protocol的简称, 中文名是用户数据报协议,是OSI参考模型中一种无连接的传输层协议,提供面向事务的简单不可靠信息传送服务,IETF RFC 768是UDP的正式规范。UDP在IP报文的协议号是17。
c、ICMP是Internet控制报文协议。它是TCP/IP协议簇的一个子协议,用于在IP主机、路由器之间传递控制消息。控制消息是指网络通不通、主机是否可达、路由是否可用等网络本身的消息。这些控制消息虽然并不传输用户数据,但是对于用户数据的传递起着重要的作用。
tcp,udp都是dao网络传输协议,承载数制据包传输的。
tcp是可靠bai传输,有du3次握手机制保证zhi数据传输的可靠性。如果dao有丢包,则重新传数据。想FTP文件传送,远程登录,POP3电子邮件,这些都是基于TCP协议的,他们要保证传输的完整性。
udp实时性较强,但可靠性不强,有丢包还继续传输,通常想语音,电话,视频是udp传输,偶尔丢几个包不影响通信。
icmp是TCP/IP协议簇的一个子协议。不承载数据,不是用来传输用户数据,是用来传递控制消息的,即:网络通不通、主机是否可达。ping命令就是基于ICMP的。(https://zhidao.baidu.com/question/342438578.html?qbl=relate_question_0&word=icmp%2Ctcp%2Cudp%CA%C7%CA%B2%C3%B4)
5、删除INPUT规则链中加入的允许ICMP流量,并把默认策略设置为允许:
[root@linuxprobe ~]# iptables -L | head
Chain INPUT (policy DROP)
target prot opt source destination
ACCEPT icmp -- anywhere anywhere
Chain FORWARD (policy ACCEPT)
target prot opt source destination
Chain OUTPUT (policy ACCEPT)
target prot opt source destination
[root@linuxprobe ~]# iptables -D INPUT 1 ## 删除第一条规则链
[root@linuxprobe ~]# iptables -L | head ## 查看,红色部分已经删除
Chain INPUT (policy DROP)
target prot opt source destination
Chain FORWARD (policy ACCEPT)
target prot opt source destination
Chain OUTPUT (policy ACCEPT)
target prot opt source destination
Chain FORWARD_IN_ZONES (0 references)
[root@linuxprobe ~]# iptables -P INPUT ACCEPT ## -P表示设置默认策略,设置为接受
[root@linuxprobe ~]# iptables -L | head ## 查看
Chain INPUT (policy ACCEPT)
target prot opt source destination
Chain FORWARD (policy ACCEPT)
target prot opt source destination
Chain OUTPUT (policy ACCEPT)
target prot opt source destination
Chain FORWARD_IN_ZONES (0 references)
6、将INPUT规则链设置为只允许指定网段的主机访问本机的22端口,拒绝来自其他所有主机的流量
设置前测试:
[root@linuxprobe ~]# ifconfig | head ## 查看当前的IP
eno16777728: flags=4163<UP,BROADCAST,RUNNING,MULTICAST> mtu 1500
inet 192.168.3.13 netmask 255.255.255.0 broadcast 192.168.3.255
inet6 fe80::20c:29ff:feab:7b00 prefixlen 64 scopeid 0x20<link>
ether 00:0c:29:ab:7b:00 txqueuelen 1000 (Ethernet)
RX packets 878 bytes 81887 (79.9 KiB)
RX errors 0 dropped 0 overruns 0 frame 0
TX packets 598 bytes 82993 (81.0 KiB)
TX errors 0 dropped 0 overruns 0 carrier 0 collisions 0
lo: flags=73<UP,LOOPBACK,RUNNING> mtu 65536
[root@linuxprobe ~]# ifconfig | head ## 登录另一台虚拟机,查看IP
ens160: flags=4163<UP,BROADCAST,RUNNING,MULTICAST> mtu 1500
inet 192.168.3.14 netmask 255.255.255.0 broadcast 192.168.3.255
inet6 fe80::d7fe:9dfc:42ec:c255 prefixlen 64 scopeid 0x20<link>
ether 00:0c:29:ef:86:f2 txqueuelen 1000 (Ethernet)
RX packets 6387 bytes 689901 (673.7 KiB)
RX errors 0 dropped 0 overruns 0 frame 0
TX packets 5564 bytes 625924 (611.2 KiB)
TX errors 0 dropped 0 overruns 0 carrier 0 collisions 0
lo: flags=73<UP,LOOPBACK,RUNNING> mtu 65536
[root@linuxprobe ~]# ssh 192.168.3.13 ## 远程连接,通过
root@192.168.3.13's password:
Last login: Fri Oct 30 14:31:33 2020
[root@linuxprobe ~]# ifconfig | head ## 登录另一台虚拟机,查看IP
ens160: flags=4163<UP,BROADCAST,RUNNING,MULTICAST> mtu 1500
inet 192.168.3.8 netmask 255.255.255.0 broadcast 192.168.3.255
inet6 fe80::54f8:bbf7:7760:3745 prefixlen 64 scopeid 0x20<link>
ether 00:0c:29:8d:79:f8 txqueuelen 1000 (Ethernet)
RX packets 98 bytes 15531 (15.1 KiB)
RX errors 0 dropped 0 overruns 0 frame 0
TX packets 94 bytes 14709 (14.3 KiB)
TX errors 0 dropped 0 overruns 0 carrier 0 collisions 0
lo: flags=73<UP,LOOPBACK,RUNNING> mtu 65536
[root@linuxprobe ~]# ssh 192.168.3.13 ## 远程连接,通过
root@192.168.3.13's password:
Last login: Fri Oct 30 15:06:39 2020 from 192.168.3.14
将INPUT规则链设置为只允许指定网段的主机访问本机的22端口,拒绝其他所有主机的流量:
[root@linuxprobe ~]# iptables -L | head ## 查看
Chain INPUT (policy ACCEPT)
target prot opt source destination
Chain FORWARD (policy ACCEPT)
target prot opt source destination
Chain OUTPUT (policy ACCEPT)
target prot opt source destination
Chain FORWARD_IN_ZONES (0 references)
[root@linuxprobe ~]# iptables -I INPUT -s 192.168.10.0/24 -p tcp --dport 22 -j ACCEPT
## 允许部分网段 -s表示匹配来源地址IP/MASK, -p表示匹配协议,--dport表示匹配目标端口号,-I表示在规则链的头部加入新规则
[root@linuxprobe ~]# iptables -L | head ## 查看设置效果
Chain INPUT (policy ACCEPT)
target prot opt source destination
ACCEPT tcp -- 192.168.10.0/24 anywhere tcp dpt:ssh
Chain FORWARD (policy ACCEPT)
target prot opt source destination
Chain OUTPUT (policy ACCEPT)
target prot opt source destination
[root@linuxprobe ~]# iptables -A INPUT -p tcp --dport 22 -j REJECT ## 拒绝其他所有主机流量,-A表示在规则链的尾部加入新规则,-p表示匹配协议,--dport表示匹配目标端口号
[root@linuxprobe ~]# iptables -L | head ## 查看设置效果
Chain INPUT (policy ACCEPT)
target prot opt source destination
ACCEPT tcp -- 192.168.10.0/24 anywhere tcp dpt:ssh
REJECT tcp -- anywhere anywhere tcp dpt:ssh reject-with icmp-port-unreachable
Chain FORWARD (policy ACCEPT)
target prot opt source destination
Chain OUTPUT (policy ACCEPT)
target prot opt source destination
注:防火墙策略规则是按照从上到下的顺序匹配的,因此一定要把允许动作放到拒绝动作前面,否则所有的流量就被拒绝掉了。
测试设置后的远程连接效果:
[root@linuxprobe ~]# ifconfig | head ## 登录另外一台主机,查看IP
ens160: flags=4163<UP,BROADCAST,RUNNING,MULTICAST> mtu 1500
inet 192.168.3.14 netmask 255.255.255.0 broadcast 192.168.3.255
inet6 fe80::d7fe:9dfc:42ec:c255 prefixlen 64 scopeid 0x20<link>
ether 00:0c:29:ef:86:f2 txqueuelen 1000 (Ethernet)
RX packets 164 bytes 21581 (21.0 KiB)
RX errors 0 dropped 0 overruns 0 frame 0
TX packets 137 bytes 18893 (18.4 KiB)
TX errors 0 dropped 0 overruns 0 carrier 0 collisions 0
lo: flags=73<UP,LOOPBACK,RUNNING> mtu 65536
[root@linuxprobe ~]# ssh 192.168.3.13 ## 测试远程连接,失败
ssh: connect to host 192.168.3.13 port 22: Connection refused
[root@linuxprobe ~]# ifconfig | head ## 登录另一台主机,查看IP
ens160: flags=4163<UP,BROADCAST,RUNNING,MULTICAST> mtu 1500
inet 192.168.3.8 netmask 255.255.255.0 broadcast 192.168.3.255
inet6 fe80::54f8:bbf7:7760:3745 prefixlen 64 scopeid 0x20<link>
ether 00:0c:29:8d:79:f8 txqueuelen 1000 (Ethernet)
RX packets 372 bytes 48040 (46.9 KiB)
RX errors 0 dropped 0 overruns 0 frame 0
TX packets 229 bytes 33472 (32.6 KiB)
TX errors 0 dropped 0 overruns 0 carrier 0 collisions 0
lo: flags=73<UP,LOOPBACK,RUNNING> mtu 65536
[root@linuxprobe ~]# ssh 192.168.3.13 ## 测试远程连接,失败
ssh: connect to host 192.168.3.13 port 22: Connection refused
删除以上允许指定网段主机访问本机22端口、拒绝其他所有主句流量的设置:
[root@linuxprobe ~]# iptables -L | head ## 查看当前防火墙规则链
Chain INPUT (policy ACCEPT)
target prot opt source destination
ACCEPT tcp -- 192.168.10.0/24 anywhere tcp dpt:ssh
REJECT tcp -- anywhere anywhere tcp dpt:ssh reject-with icmp-port-unreachable
Chain FORWARD (policy ACCEPT)
target prot opt source destination
Chain OUTPUT (policy ACCEPT)
target prot opt source destination
[root@linuxprobe ~]# iptables -D INPUT 1 ## 删除第一个
[root@linuxprobe ~]# iptables -L | head ## 查看
Chain INPUT (policy ACCEPT)
target prot opt source destination
REJECT tcp -- anywhere anywhere tcp dpt:ssh reject-with icmp-port-unreachable
Chain FORWARD (policy ACCEPT)
target prot opt source destination
Chain OUTPUT (policy ACCEPT)
target prot opt source destination
[root@linuxprobe ~]# iptables -D INPUT 1 ## 删除第一个
[root@linuxprobe ~]# iptables -L | head ## 查看,两个都已经删除
Chain INPUT (policy ACCEPT)
target prot opt source destination
Chain FORWARD (policy ACCEPT)
target prot opt source destination
Chain OUTPUT (policy ACCEPT)
target prot opt source destination
Chain FORWARD_IN_ZONES (0 references)
重新设置允许指定网段主机访问本机的22端口,拒绝其他主机流量:
[root@linuxprobe ~]# iptables -L | head ## 查看当前规则链
Chain INPUT (policy ACCEPT)
target prot opt source destination
Chain FORWARD (policy ACCEPT)
target prot opt source destination
Chain OUTPUT (policy ACCEPT)
target prot opt source destination
Chain FORWARD_IN_ZONES (0 references)
[root@linuxprobe ~]# iptables -I INPUT -s 192.168.3.0/24 -p tcp --dport 22 -j ACCEPT ## 设置允许网段
[root@linuxprobe ~]# iptables -L | head ## 查看
Chain INPUT (policy ACCEPT)
target prot opt source destination
ACCEPT tcp -- 192.168.3.0/24 anywhere tcp dpt:ssh
Chain FORWARD (policy ACCEPT)
target prot opt source destination
Chain OUTPUT (policy ACCEPT)
target prot opt source destination
[root@linuxprobe ~]# iptables -A INPUT -p tcp --dport 22 -j REJECT ## 拒绝其他主机流量
[root@linuxprobe ~]# iptables -L | head ## 查看
Chain INPUT (policy ACCEPT)
target prot opt source destination
ACCEPT tcp -- 192.168.3.0/24 anywhere tcp dpt:ssh
REJECT tcp -- anywhere anywhere tcp dpt:ssh reject-with icmp-port-unreachable
Chain FORWARD (policy ACCEPT)
target prot opt source destination
Chain OUTPUT (policy ACCEPT)
target prot opt source destination
测试设置效果:
[root@linuxprobe ~]# ifconfig | head ## 登录另一台主句,查看ip
ens160: flags=4163<UP,BROADCAST,RUNNING,MULTICAST> mtu 1500
inet 192.168.3.14 netmask 255.255.255.0 broadcast 192.168.3.255
inet6 fe80::d7fe:9dfc:42ec:c255 prefixlen 64 scopeid 0x20<link>
ether 00:0c:29:ef:86:f2 txqueuelen 1000 (Ethernet)
RX packets 230 bytes 27797 (27.1 KiB)
RX errors 0 dropped 0 overruns 0 frame 0
TX packets 179 bytes 23712 (23.1 KiB)
TX errors 0 dropped 0 overruns 0 carrier 0 collisions 0
lo: flags=73<UP,LOOPBACK,RUNNING> mtu 65536
[root@linuxprobe ~]# ssh 192.168.3.13 ## 测试远程连接,成功
root@192.168.3.13's password:
Last login: Fri Oct 30 15:09:27 2020 from 192.168.3.8
[root@linuxprobe ~]# ifconfig | head ## 登录另一台主句,查看IP
ens160: flags=4163<UP,BROADCAST,RUNNING,MULTICAST> mtu 1500
inet 192.168.3.8 netmask 255.255.255.0 broadcast 192.168.3.255
inet6 fe80::54f8:bbf7:7760:3745 prefixlen 64 scopeid 0x20<link>
ether 00:0c:29:8d:79:f8 txqueuelen 1000 (Ethernet)
RX packets 438 bytes 54337 (53.0 KiB)
RX errors 0 dropped 0 overruns 0 frame 0
TX packets 260 bytes 37486 (36.6 KiB)
TX errors 0 dropped 0 overruns 0 carrier 0 collisions 0
lo: flags=73<UP,LOOPBACK,RUNNING> mtu 65536
[root@linuxprobe ~]# ssh 192.168.3.13 ## 测试远程连接,成功
root@192.168.3.13's password:
Last login: Fri Oct 30 15:36:17 2020 from 192.168.3.14
删除设置:
[root@linuxprobe ~]# iptables -L | head ## 查看当前规则链
Chain INPUT (policy ACCEPT)
target prot opt source destination
ACCEPT tcp -- 192.168.3.0/24 anywhere tcp dpt:ssh
REJECT tcp -- anywhere anywhere tcp dpt:ssh reject-with icmp-port-unreachable
Chain FORWARD (policy ACCEPT)
target prot opt source destination
Chain OUTPUT (policy ACCEPT)
target prot opt source destination
[root@linuxprobe ~]# iptables -D INPUT 1 ## 删除第一条
[root@linuxprobe ~]# iptables -D INPUT 1 ## 删除第一条
[root@linuxprobe ~]# iptables -L | head ## 查看规则链
Chain INPUT (policy ACCEPT)
target prot opt source destination
Chain FORWARD (policy ACCEPT)
target prot opt source destination
Chain OUTPUT (policy ACCEPT)
target prot opt source destination
Chain FORWARD_IN_ZONES (0 references)
8、向INPUT规则链中添加拒绝所有人访问本机123456端口的策略规则
[root@linuxprobe ~]# iptables -L | head ## 查看规则链
Chain INPUT (policy ACCEPT)
target prot opt source destination
Chain FORWARD (policy ACCEPT)
target prot opt source destination
Chain OUTPUT (policy ACCEPT)
target prot opt source destination
Chain FORWARD_IN_ZONES (0 references)
[root@linuxprobe ~]# iptables -I INPUT -p tcp --dport 12345 -j REJECT ## 拒绝tcp协议
[root@linuxprobe ~]# iptables -L | head ## 查看
Chain INPUT (policy ACCEPT)
target prot opt source destination
REJECT tcp -- anywhere anywhere tcp dpt:italk reject-with icmp-port-unreachable
Chain FORWARD (policy ACCEPT)
target prot opt source destination
Chain OUTPUT (policy ACCEPT)
target prot opt source destination
[root@linuxprobe ~]# iptables -I INPUT -p udp --dport 12345 -j REJECT ## 拒绝udp协议
[root@linuxprobe ~]# iptables -L | head ## 查看
Chain INPUT (policy ACCEPT)
target prot opt source destination
REJECT udp -- anywhere anywhere udp dpt:italk reject-with icmp-port-unreachable
REJECT tcp -- anywhere anywhere tcp dpt:italk reject-with icmp-port-unreachable
Chain FORWARD (policy ACCEPT)
target prot opt source destination
Chain OUTPUT (policy ACCEPT)
target prot opt source destination
删除设置:
[root@linuxprobe ~]# iptables -L | head ## 查看
Chain INPUT (policy ACCEPT)
target prot opt source destination
REJECT udp -- anywhere anywhere udp dpt:italk reject-with icmp-port-unreachable
REJECT tcp -- anywhere anywhere tcp dpt:italk reject-with icmp-port-unreachable
Chain FORWARD (policy ACCEPT)
target prot opt source destination
Chain OUTPUT (policy ACCEPT)
target prot opt source destination
[root@linuxprobe ~]# iptables -D INPUT 1 ## 删除第一个
[root@linuxprobe ~]# iptables -L | head ## 查看
Chain INPUT (policy ACCEPT)
target prot opt source destination
REJECT tcp -- anywhere anywhere tcp dpt:italk reject-with icmp-port-unreachable
Chain FORWARD (policy ACCEPT)
target prot opt source destination
Chain OUTPUT (policy ACCEPT)
target prot opt source destination
[root@linuxprobe ~]# iptables -D INPUT 1 ## 删除第一个
[root@linuxprobe ~]# iptables -L | head ## 查看
Chain INPUT (policy ACCEPT)
target prot opt source destination
Chain FORWARD (policy ACCEPT)
target prot opt source destination
Chain OUTPUT (policy ACCEPT)
target prot opt source destination
Chain FORWARD_IN_ZONES (0 references)
9、向INPUT规则链中添加拒绝192.168.10.5主句访问本机80端口(web服务)的策略规则:
[root@linuxprobe ~]# iptables -L | head ## 查看规则链
Chain INPUT (policy ACCEPT)
target prot opt source destination
Chain FORWARD (policy ACCEPT)
target prot opt source destination
Chain OUTPUT (policy ACCEPT)
target prot opt source destination
Chain FORWARD_IN_ZONES (0 references)
[root@linuxprobe ~]# iptables -I INPUT -p tcp -s 192.168.10.5 --dport 80 -j REJECT ## 向INPUT规则链中添加拒绝192.168.10.5主机访问本机80端口(web服务)的策略
[root@linuxprobe ~]# iptables -L | head ## 查看
Chain INPUT (policy ACCEPT)
target prot opt source destination
REJECT tcp -- 192.168.10.5 anywhere tcp dpt:http reject-with icmp-port-unreachable
Chain FORWARD (policy ACCEPT)
target prot opt source destination
Chain OUTPUT (policy ACCEPT)
target prot opt source destination
[root@linuxprobe ~]# iptables -D INPUT 1 ## 删除设置
[root@linuxprobe ~]# iptables -L | head ## 查看
Chain INPUT (policy ACCEPT)
target prot opt source destination
Chain FORWARD (policy ACCEPT)
target prot opt source destination
Chain OUTPUT (policy ACCEPT)
target prot opt source destination
Chain FORWARD_IN_ZONES (0 references)
10、向INPUT规则链中添加拒绝所有主机访问本机1000~1024端口的策略规则
[root@linuxprobe ~]# iptables -L | head ## 查看规则链
Chain INPUT (policy ACCEPT)
target prot opt source destination
Chain FORWARD (policy ACCEPT)
target prot opt source destination
Chain OUTPUT (policy ACCEPT)
target prot opt source destination
Chain FORWARD_IN_ZONES (0 references)
[root@linuxprobe ~]# iptables -I INPUT -p tcp --dport 1000:1024 -j REJECT ## 拒绝tcp
[root@linuxprobe ~]# iptables -L | head ## 查看
Chain INPUT (policy ACCEPT)
target prot opt source destination
REJECT tcp -- anywhere anywhere tcp dpts:cadlock2:1024 reject-with icmp-port-unreachable
Chain FORWARD (policy ACCEPT)
target prot opt source destination
Chain OUTPUT (policy ACCEPT)
target prot opt source destination
[root@linuxprobe ~]# iptables -I INPUT -p udp --dport 1000:1024 -j REJECT ## 拒绝udp
[root@linuxprobe ~]# iptables -L | head ## 查看
Chain INPUT (policy ACCEPT)
target prot opt source destination
REJECT udp -- anywhere anywhere udp dpts:cadlock2:1024 reject-with icmp-port-unreachable
REJECT tcp -- anywhere anywhere tcp dpts:cadlock2:1024 reject-with icmp-port-unreachable
Chain FORWARD (policy ACCEPT)
target prot opt source destination
Chain OUTPUT (policy ACCEPT)
target prot opt source destination
11、使用iptables命令配置的防火墙规则默认在系统重启后失效,如果想让配置的防火墙策略永久生效,执行如下命令:
[root@linuxprobe ~]# service iptables save
iptables: Saving firewall rules to /etc/sysconfig/iptables:[ OK ]




 浙公网安备 33010602011771号
浙公网安备 33010602011771号